Spotter App
See demo or read blog tutorial for more information on the Spotter app.
To begin using Steampunk Spotter, visit the registration page, create an account, and verify your email.
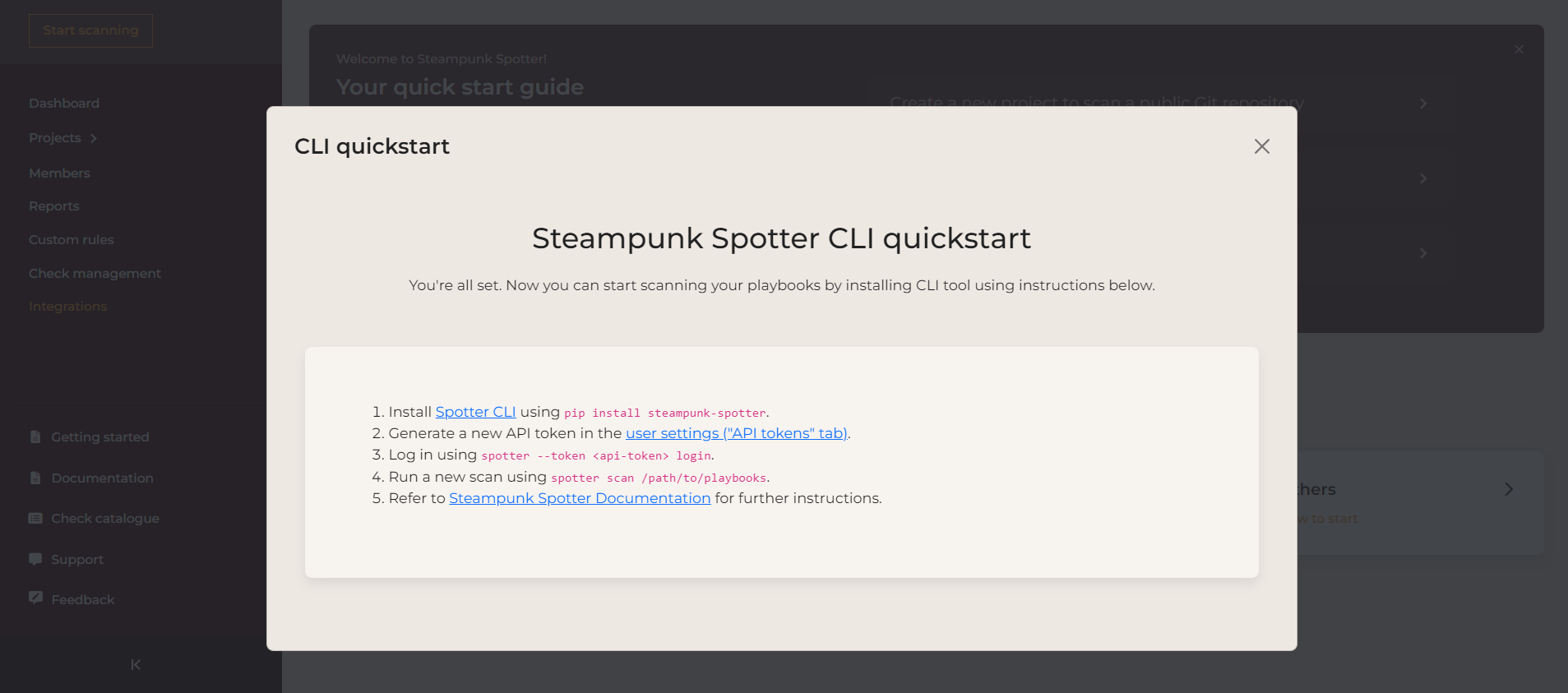
Incorporate it into your workflow using the steampunk-spotter CLI or integrate it with GitLab, GitHub Actions, or VS Code.
Requirements:
- Steampunk Spotter app user account
- steampunk-spotter CLI
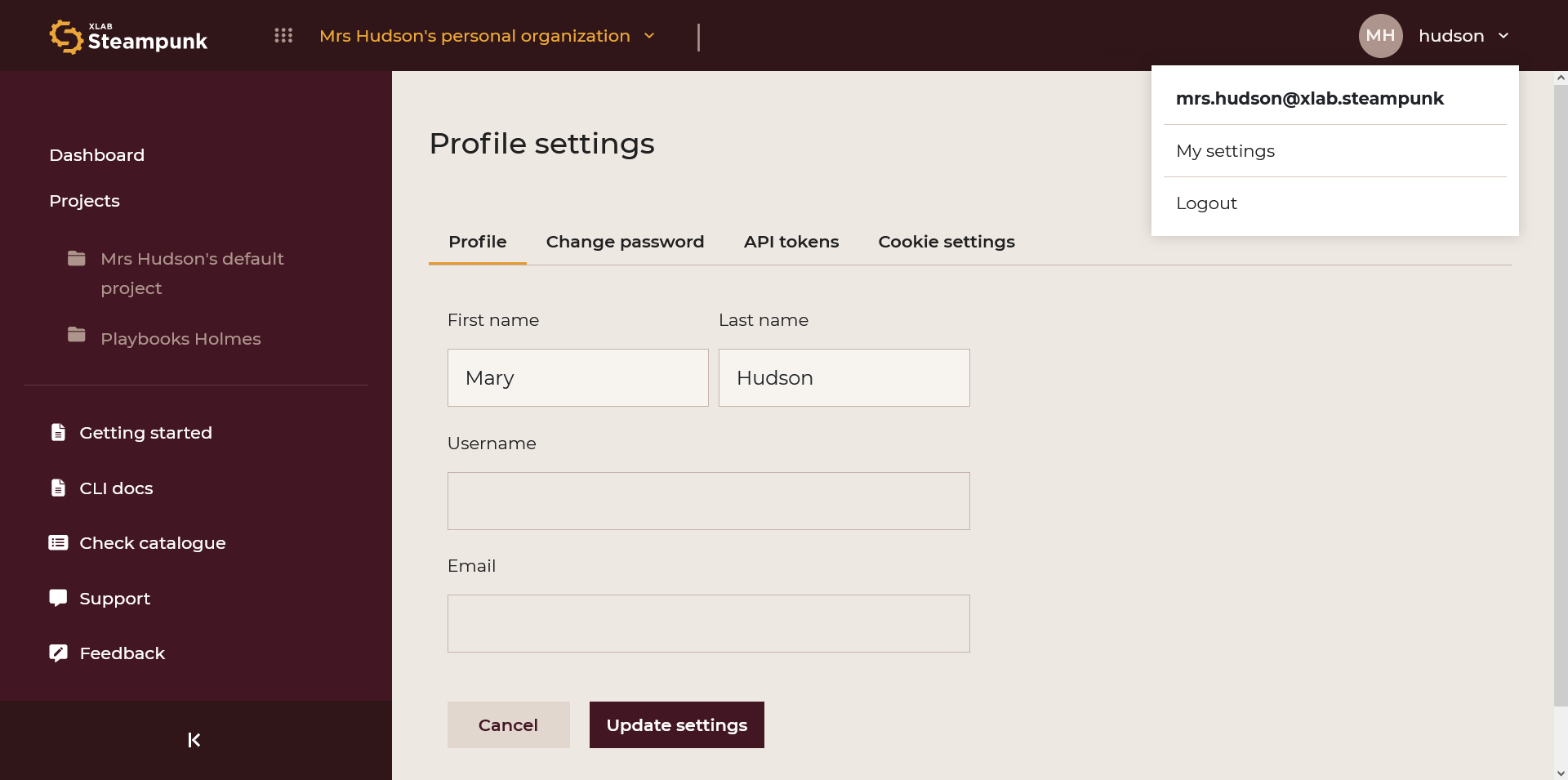
Profile Settings
By clicking your username in the upper right corner, you can choose My Settings; it will take you to your Profile settings. You can edit the fields and update them.
Profile
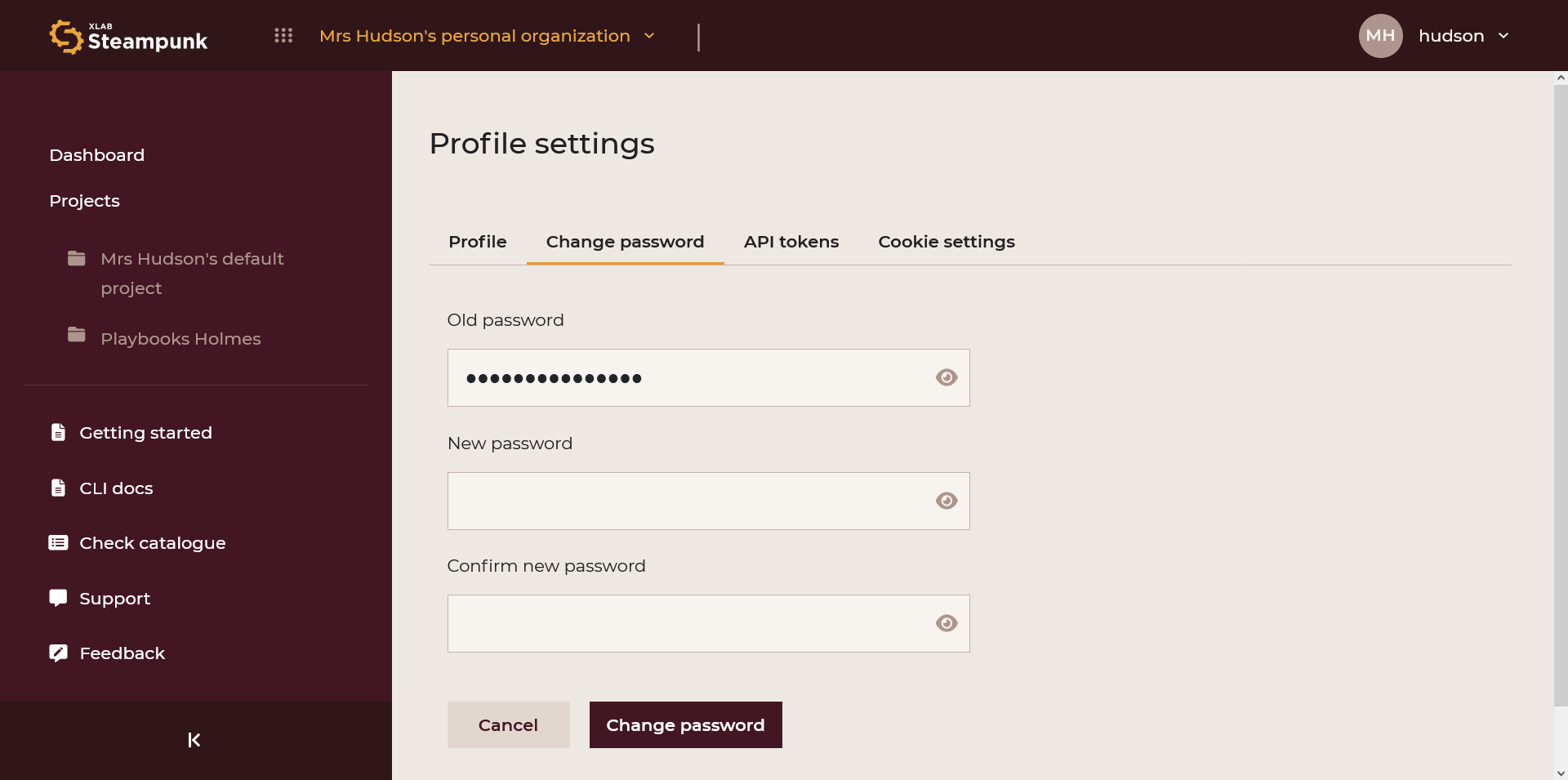
Change Password
API Tokens
Generate your API token by inputting your token name, and selecting your token expiration date. See demo.
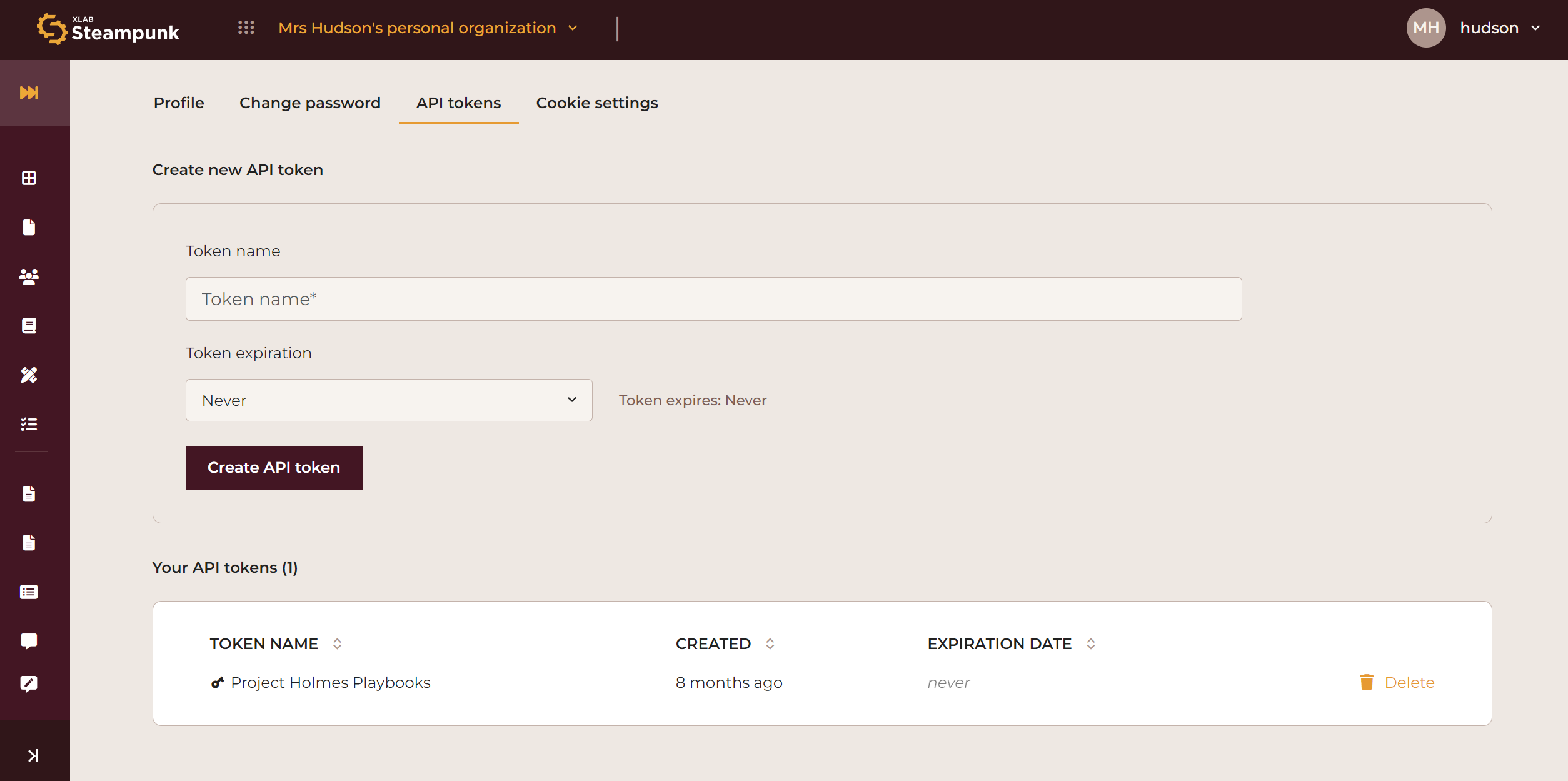
Create the API token by clicking Create API token. Make sure to copy the API token immediately; it is not possible to access it later.
Start Scanning
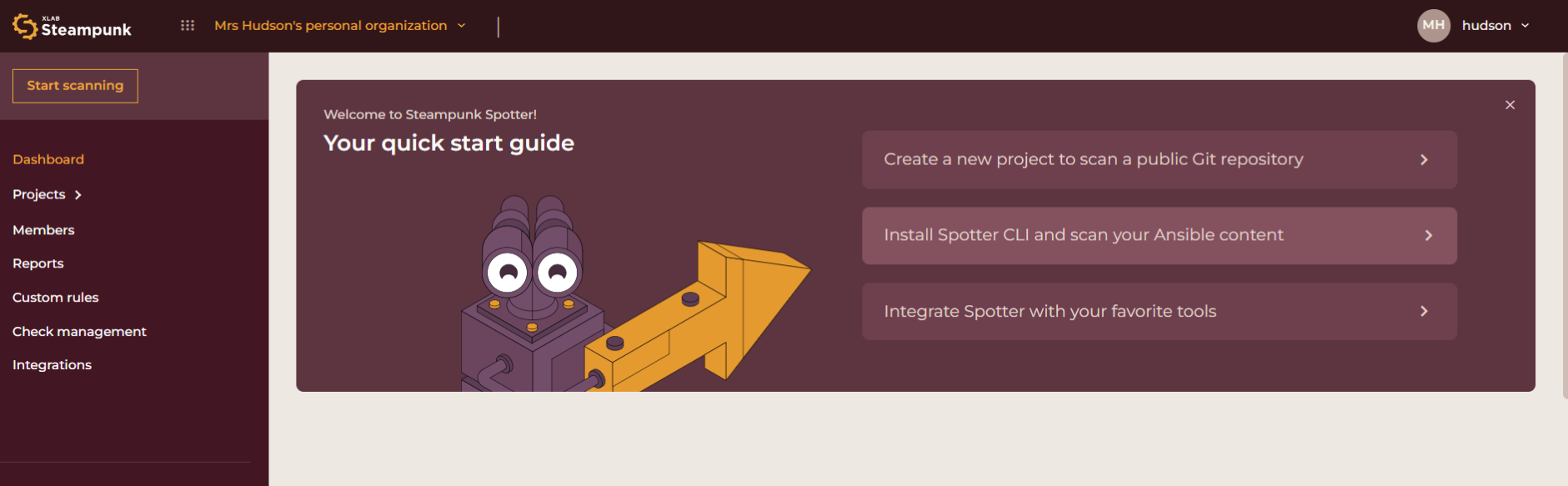
The Start Scanning section is your quick start guide to help you start scanning as quickly as possible. It features how to:
- Create a new project to scan a public Git repository
- Install Spotter CLI and scan your Ansible content
- Integrate Spotter with your favorite tools
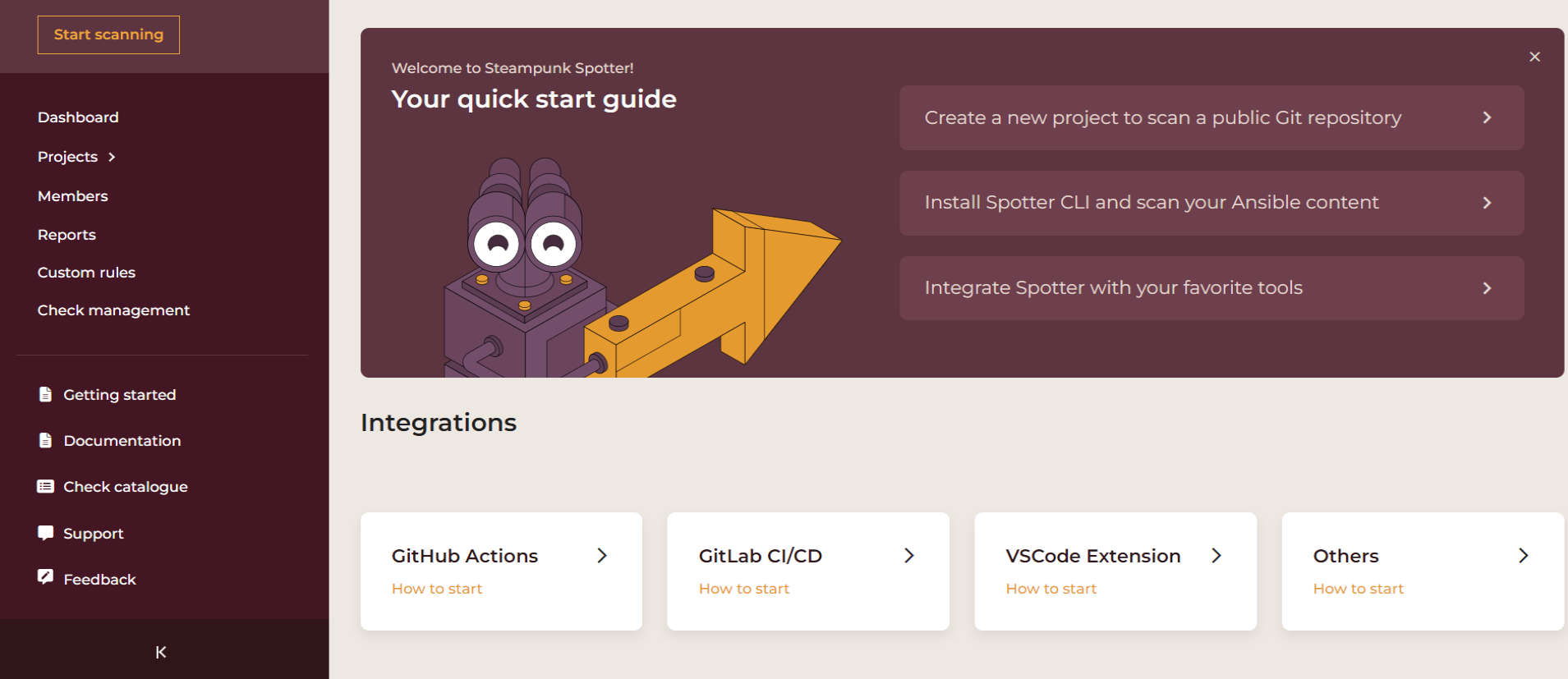
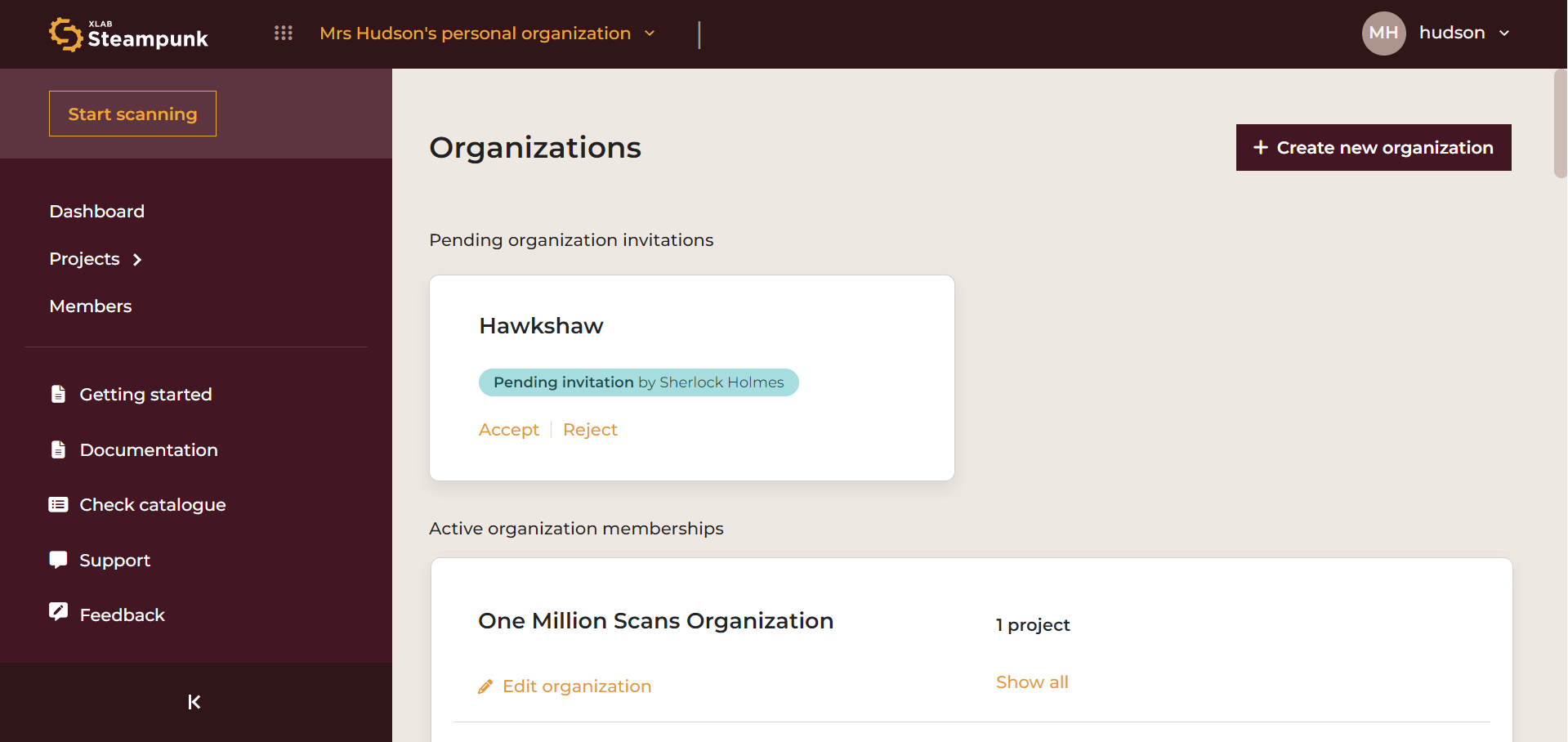
Organizations
An organization is created when you sign up.
A drop-down menu under your personal organization lets you choose an organization or view all organizations:
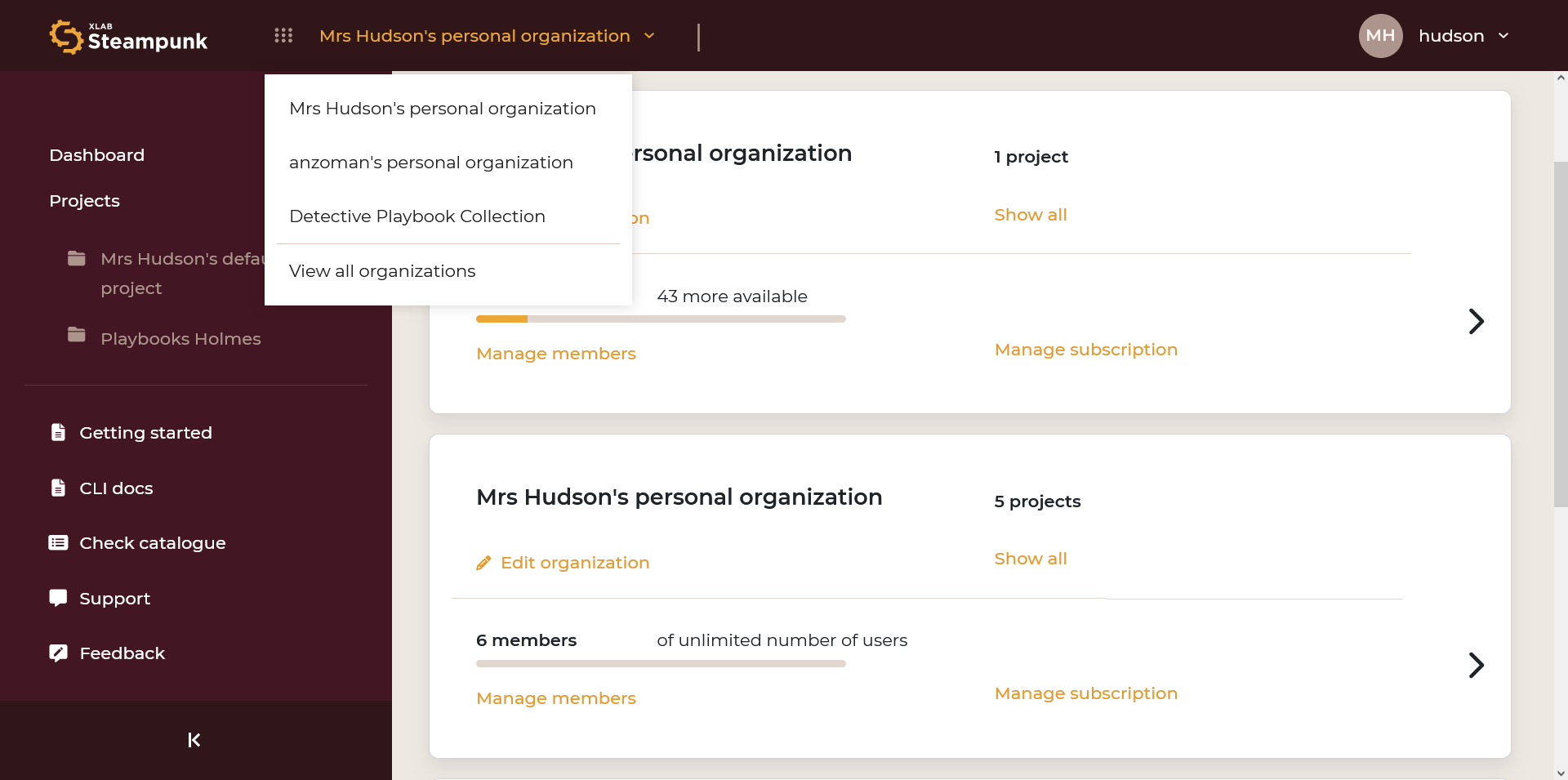
In the Organization view, you can see pending organization invitations and active organization memberships.
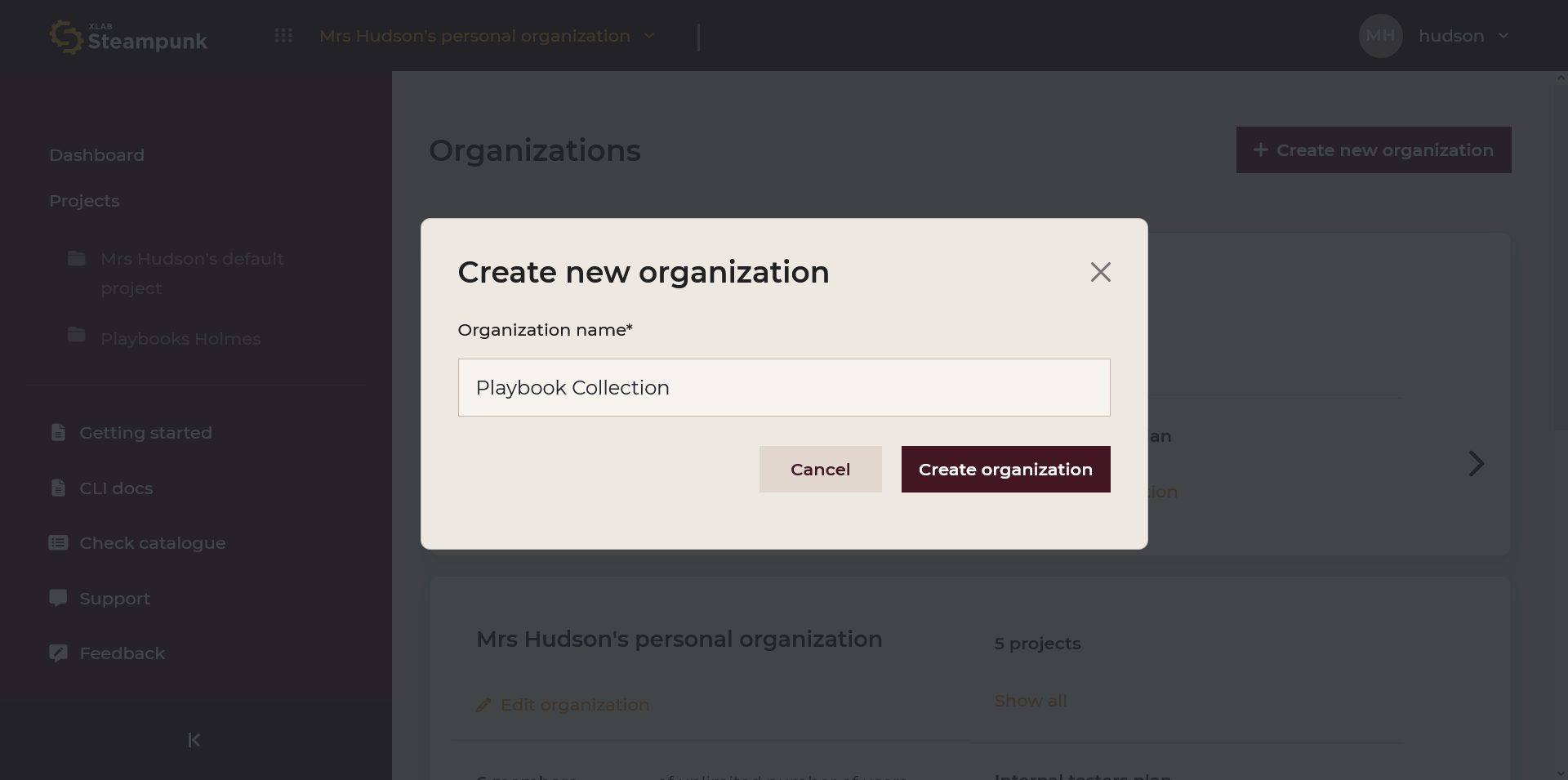
New organizations can be created by clicking Create new organization:
Dashboard
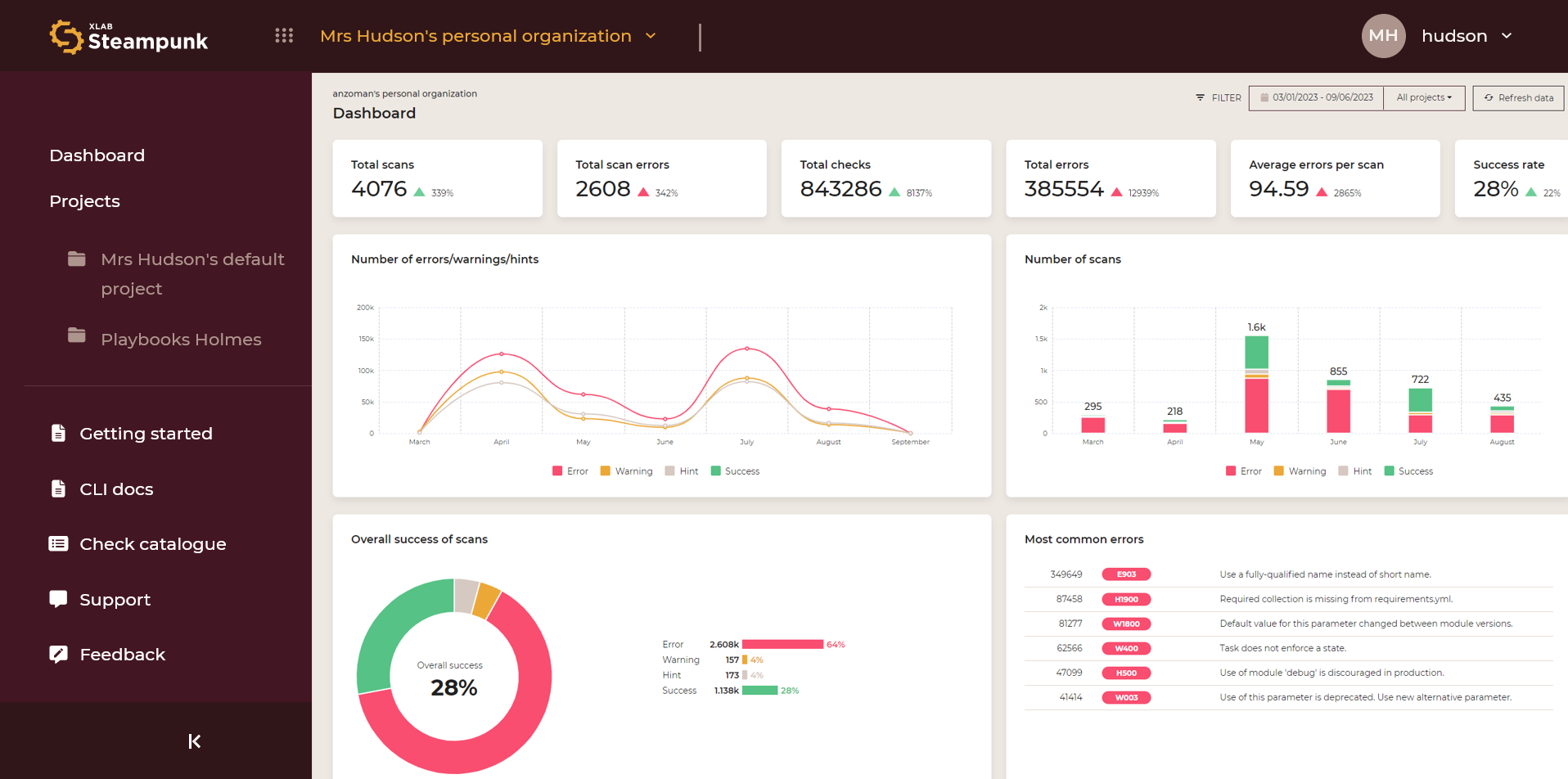
The Dashboard offers a quick snapshot of the following:
- Critical data
- Prevalent challenges
- Real-time performance tracking and success rate
It helps you stay informed about:
- Executed scans
- Error counts
- Common error patterns
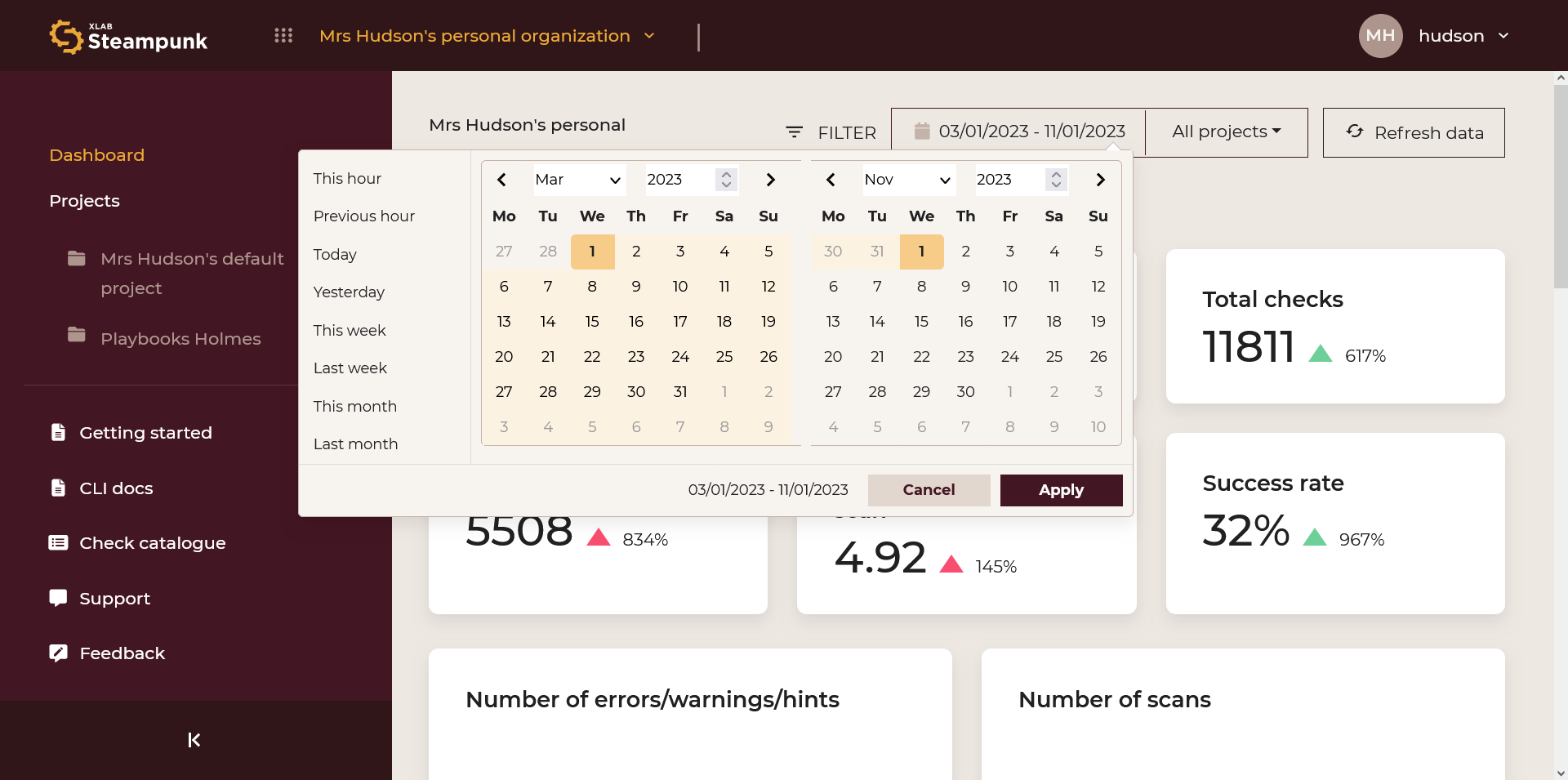
Choose a period:
Choose a project:
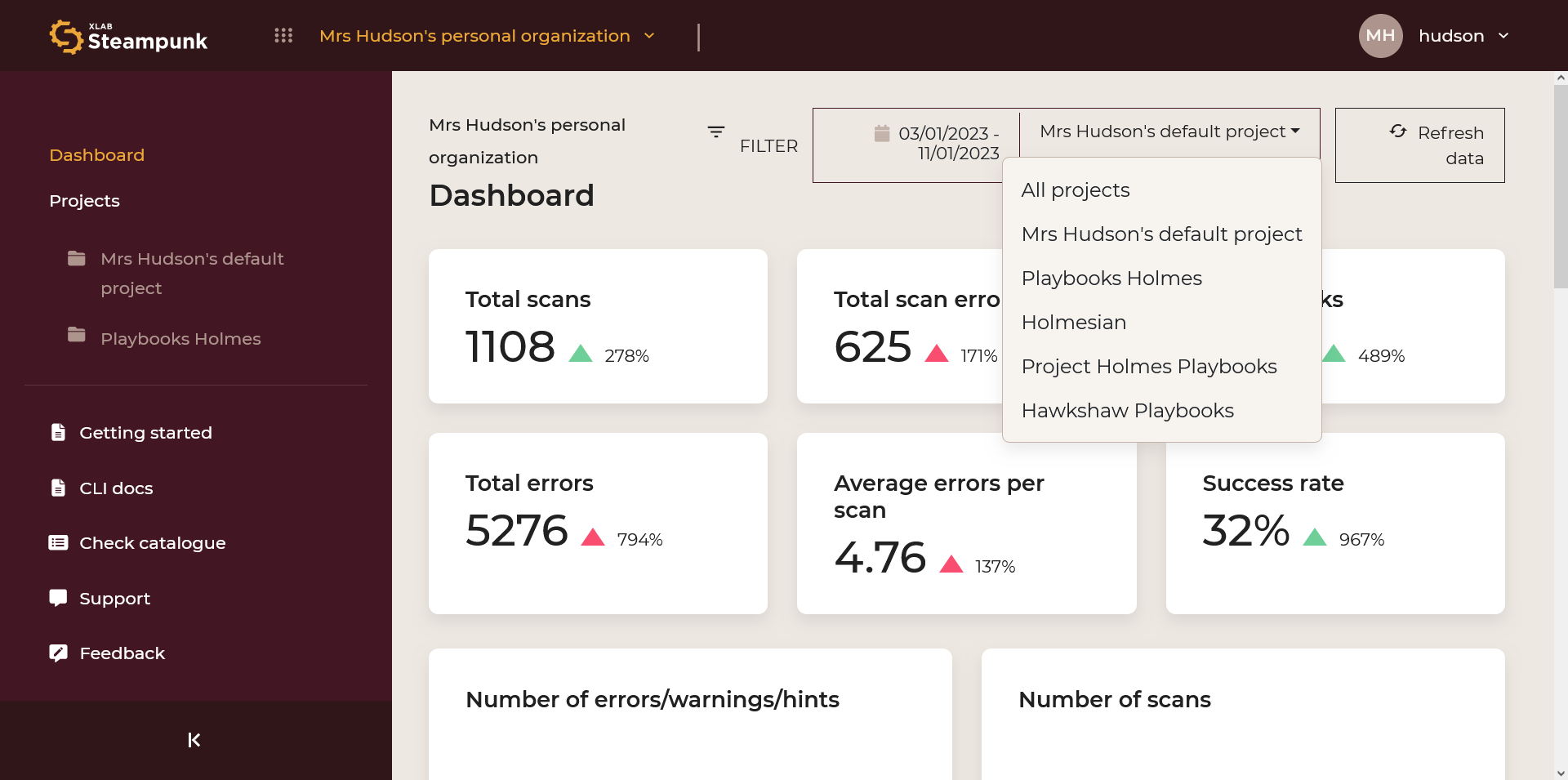
By clicking the numeric code you can access the check in the Check catalogue.
Projects
See demo on how to work with Projects.
Projects let you organize Ansible content scans. A default project is assigned to you upon sign-up; this is where your data is sent by default, no matter where you scan your Ansible content.
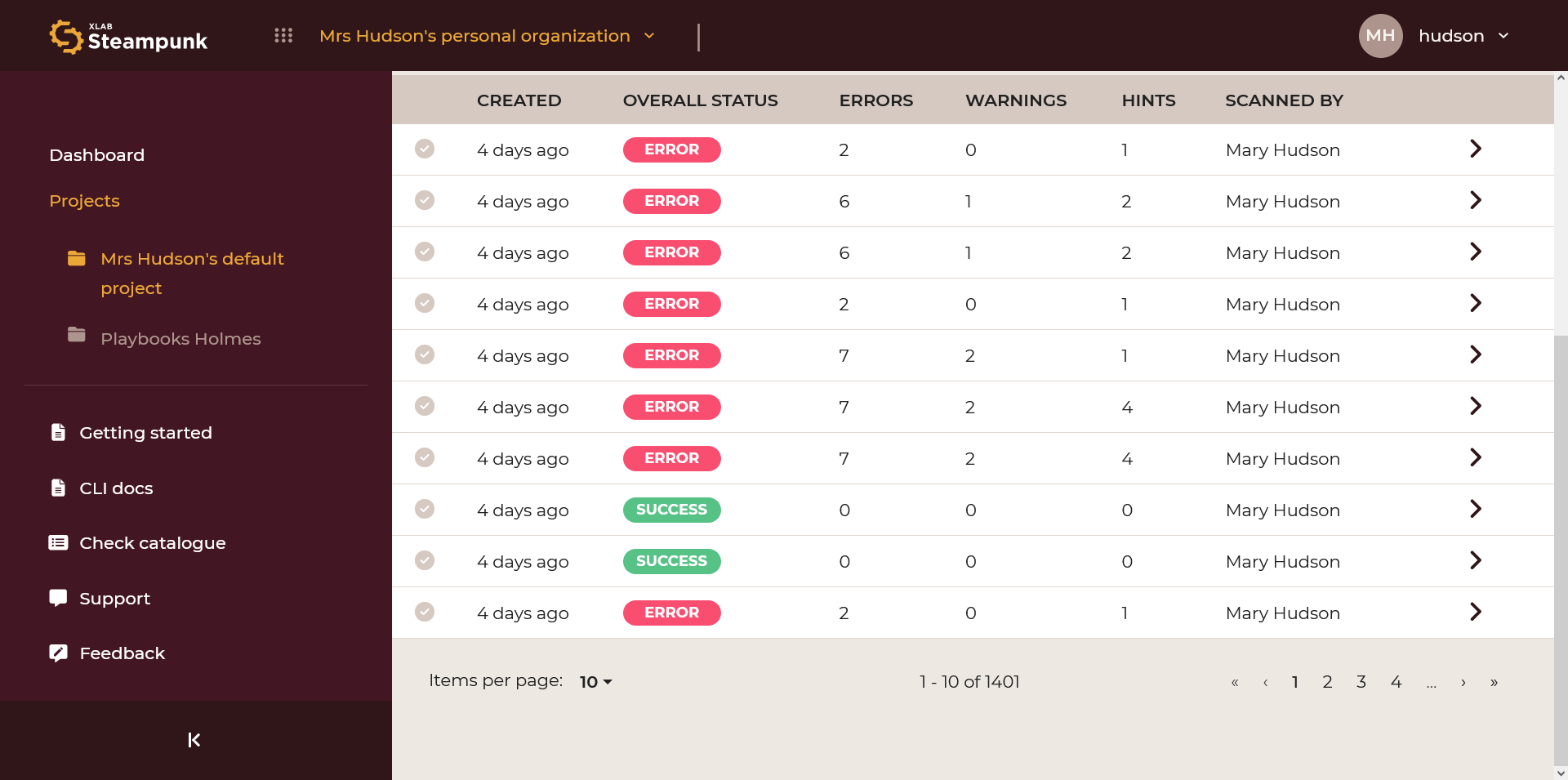
Create new Projects
New projects can be created by clicking Create project.
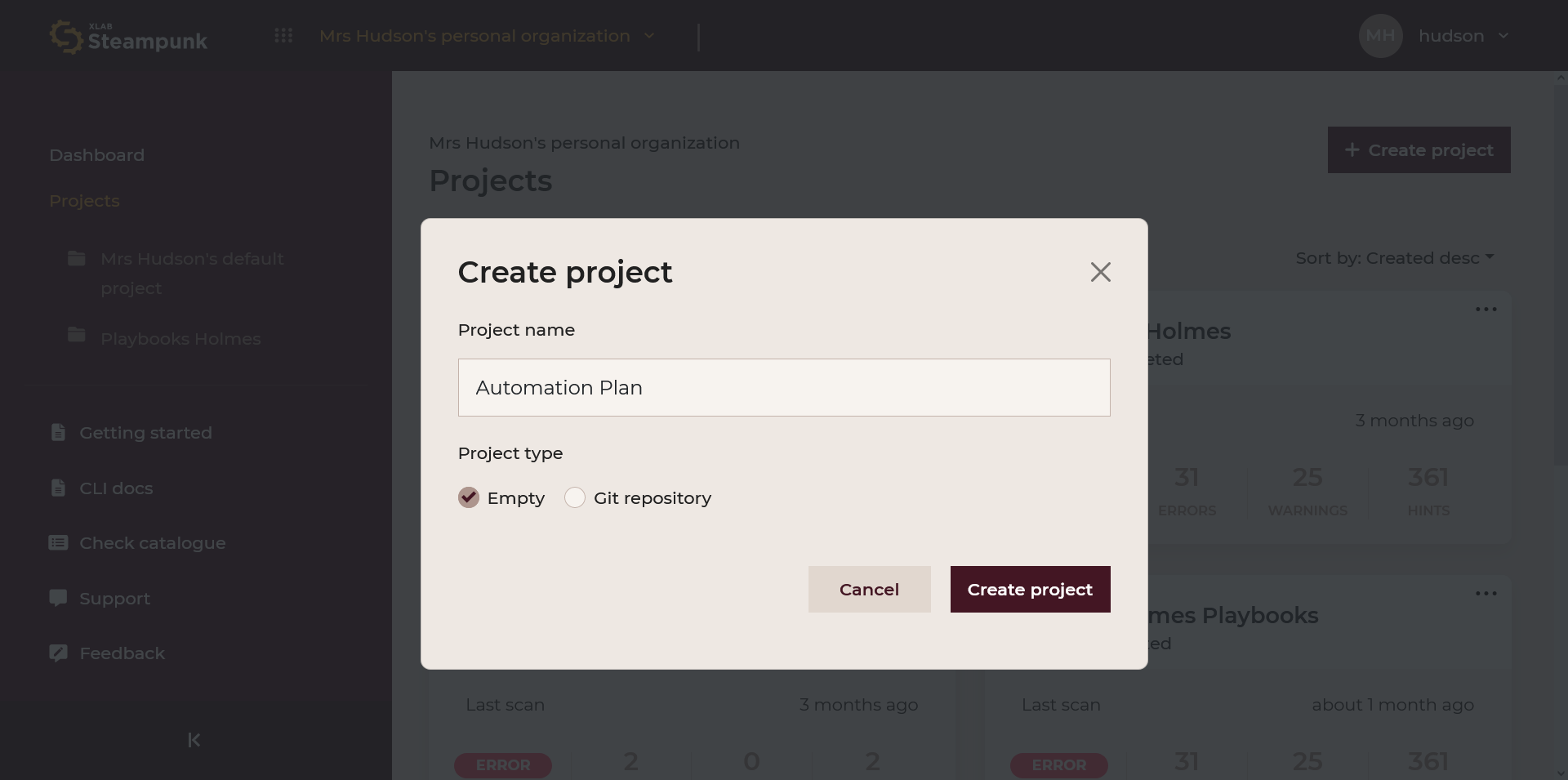
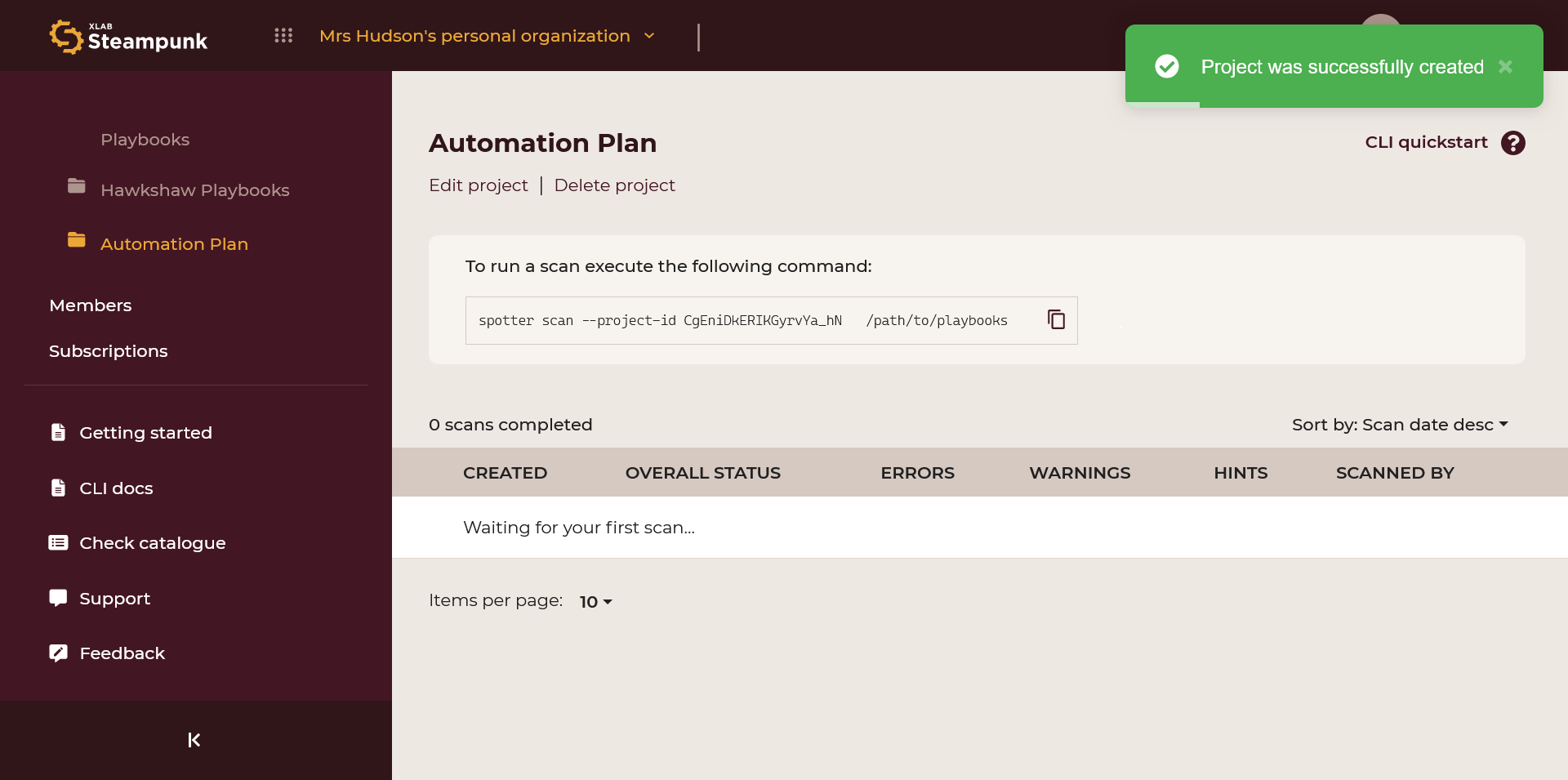
A new empty project comes with a project ID you can use to scan; Spotter sends
data to the chosen project. Copy the scan command or use the --project-id <your ID>
in the CLI. Projects can also be edited and deleted.
Git Projects
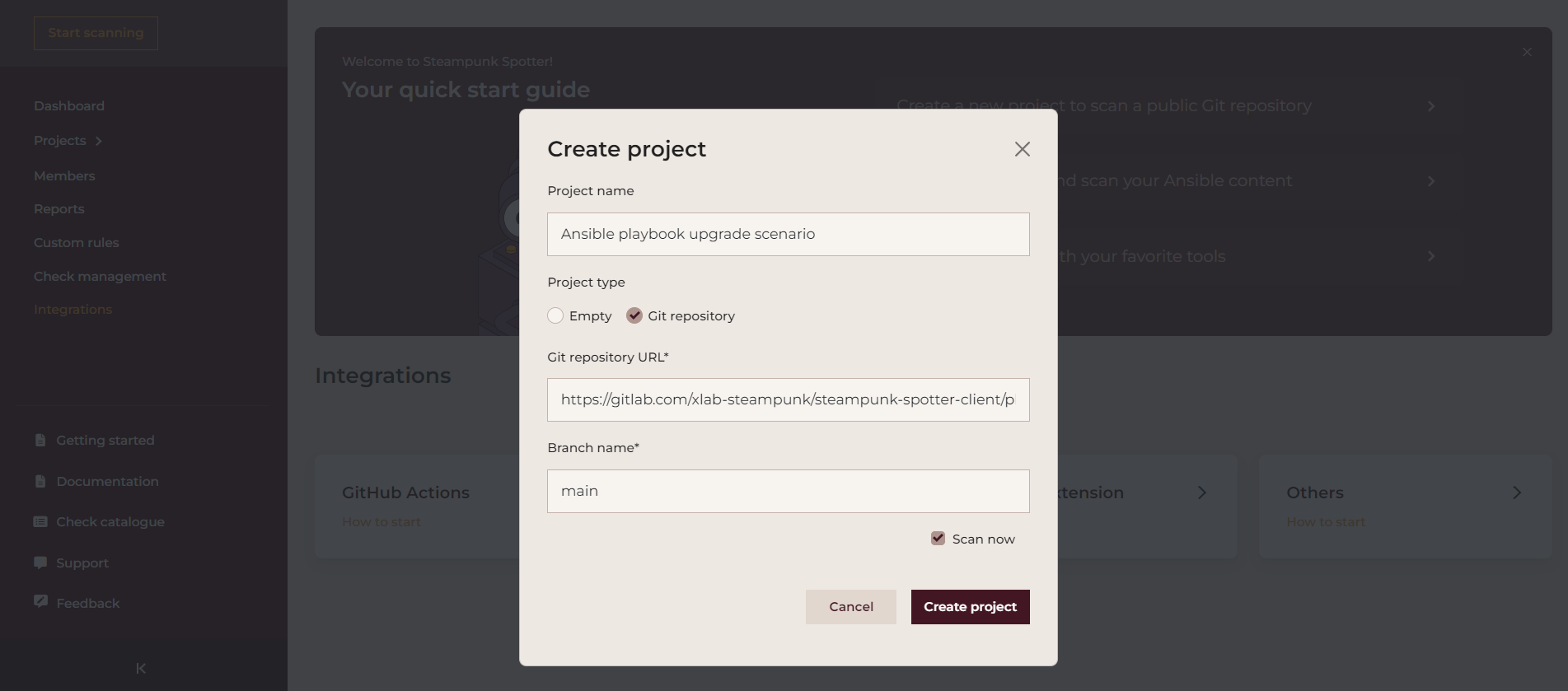
Scan a public Git repository by choosing Git repository when creating a new project. Untick the Scan now option if you do not want the scan to start right away. The action of scanning a public git repository can only be applied within the Spotter app.
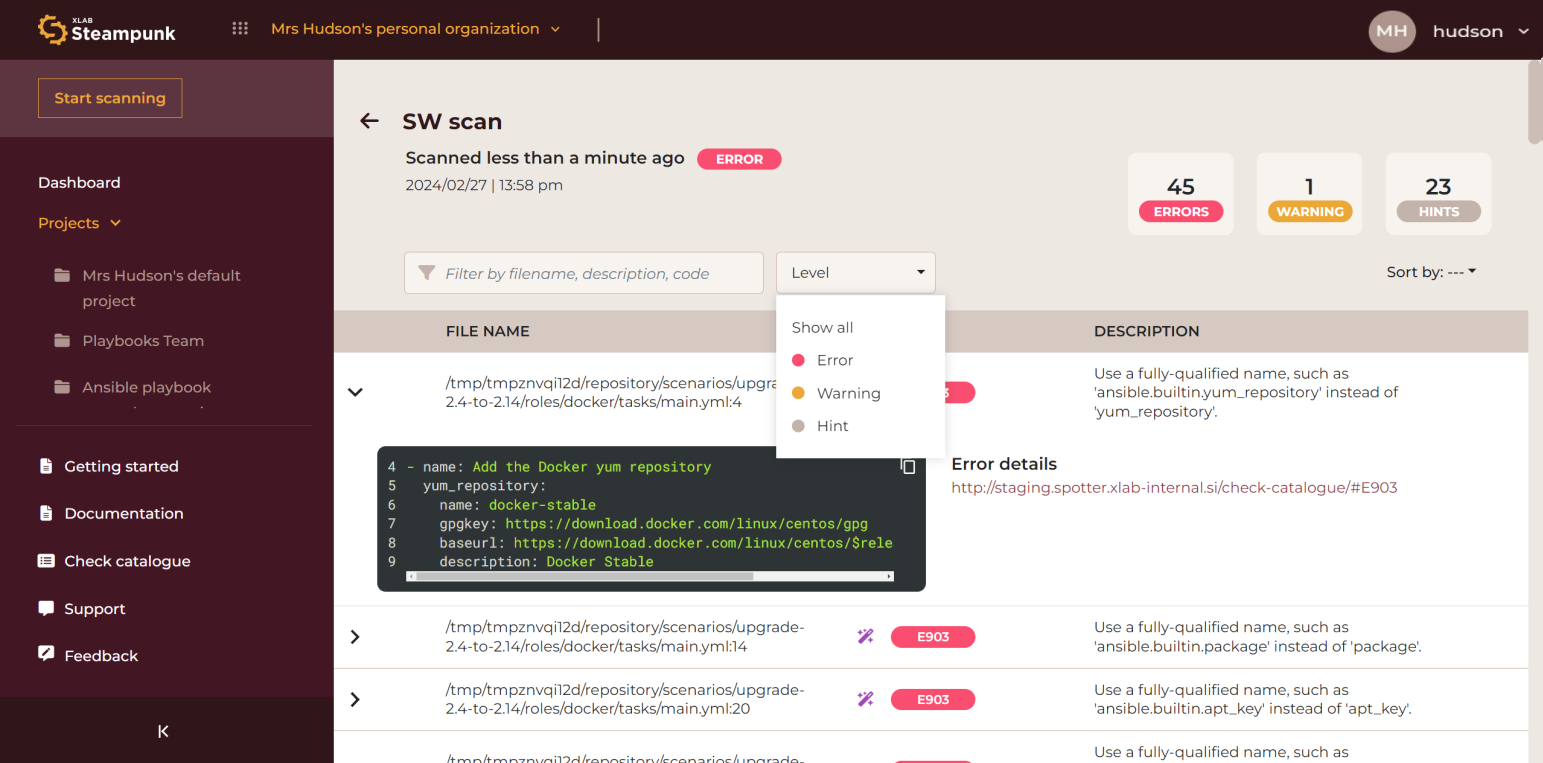
After the scan is complete, you can assess the quality of the content. You can filter by
filename, description, and code, choose the items per page shown, and choose the level of
warnings to display: errors, warnings, or hints. The information icon takes you to the
module documentation. Tapping the arrow symbol › on the left side of each line unfolds
a view of the specific section where Spotter found the highlighted issue mentioned in that
line.
Scan Environment
Steampunk Spotter captures a set of information that is relevant to each scan as it takes place. This scan environment includes Ansible and Python versions, installed collections, and Ansible configuration overrides. Tracking environments across scans enhances oversight and fortifies infrastructure management.
The scan environment is accessible within every given project by clicking the Scan environment button in the upper left corner:
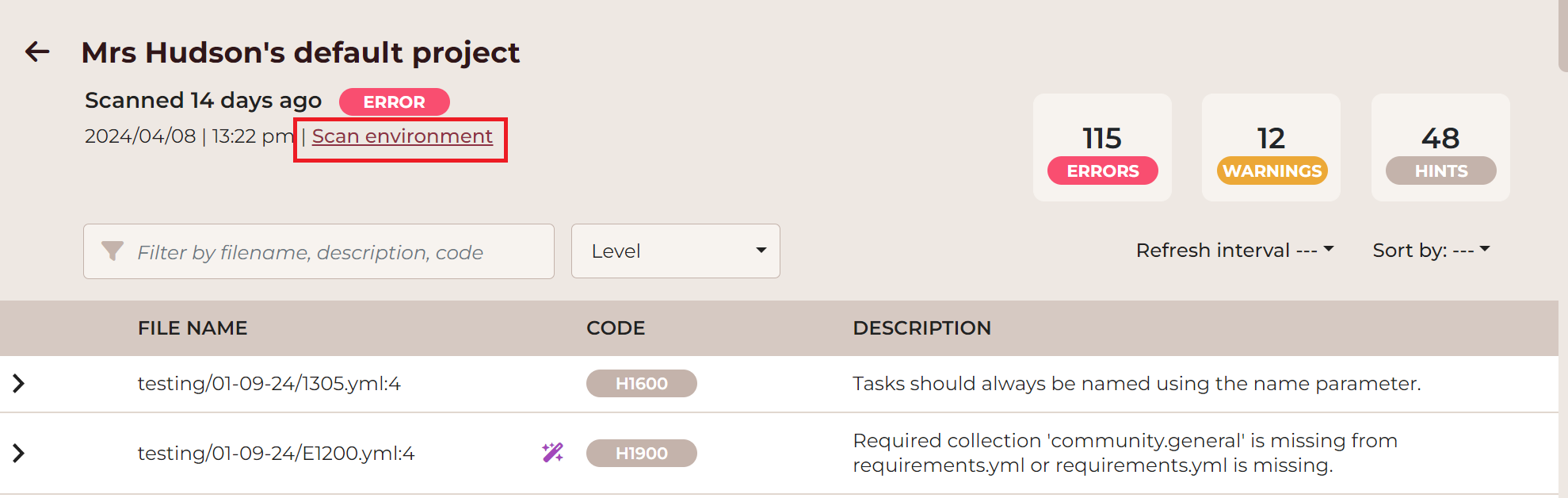
This opens a pop-up window that displays the details of your scan environment:
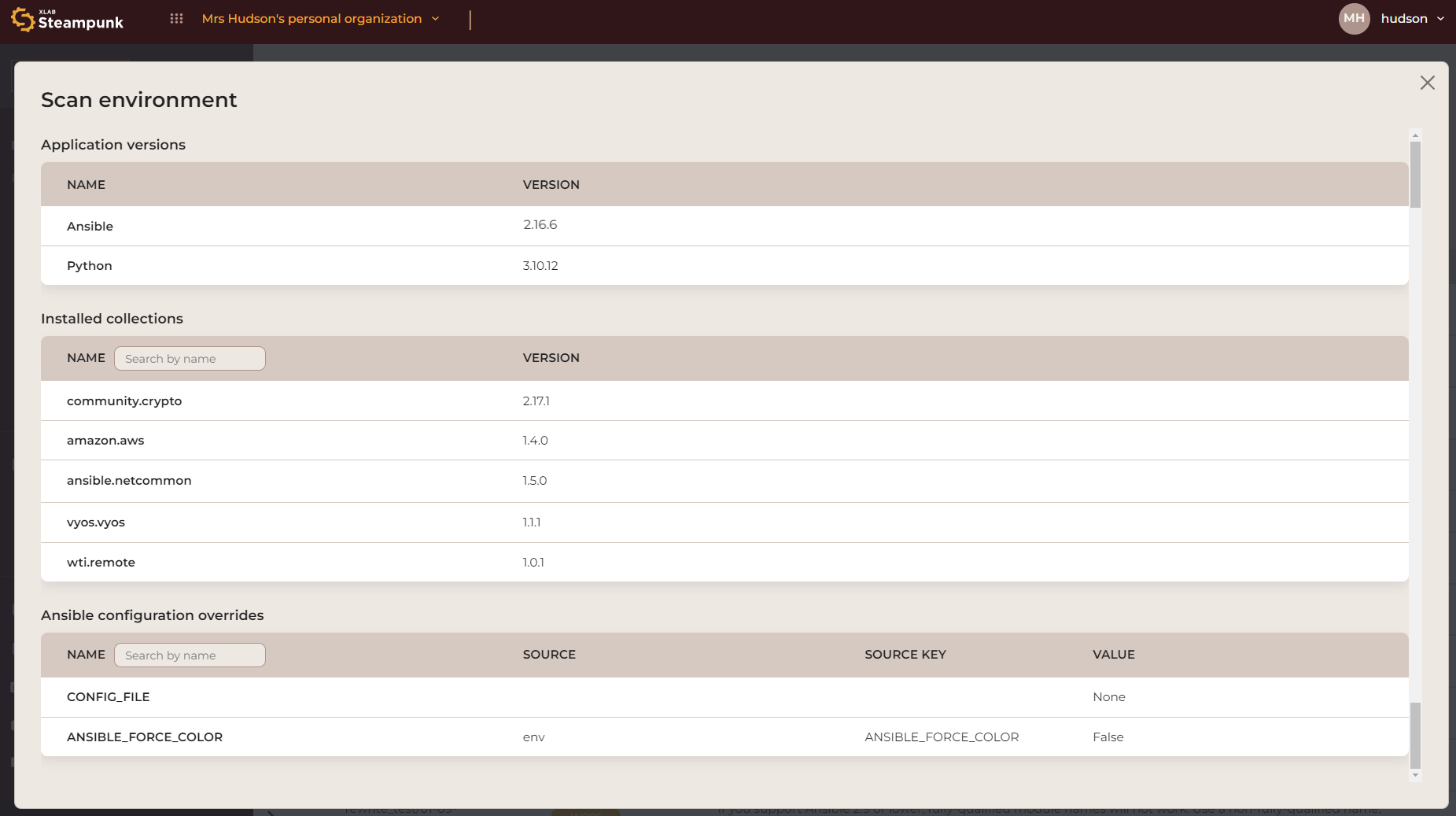
Members
In the Members section, you can see all the members of your organization; You can change organization roles by clicking on the Member role drop-down menu.
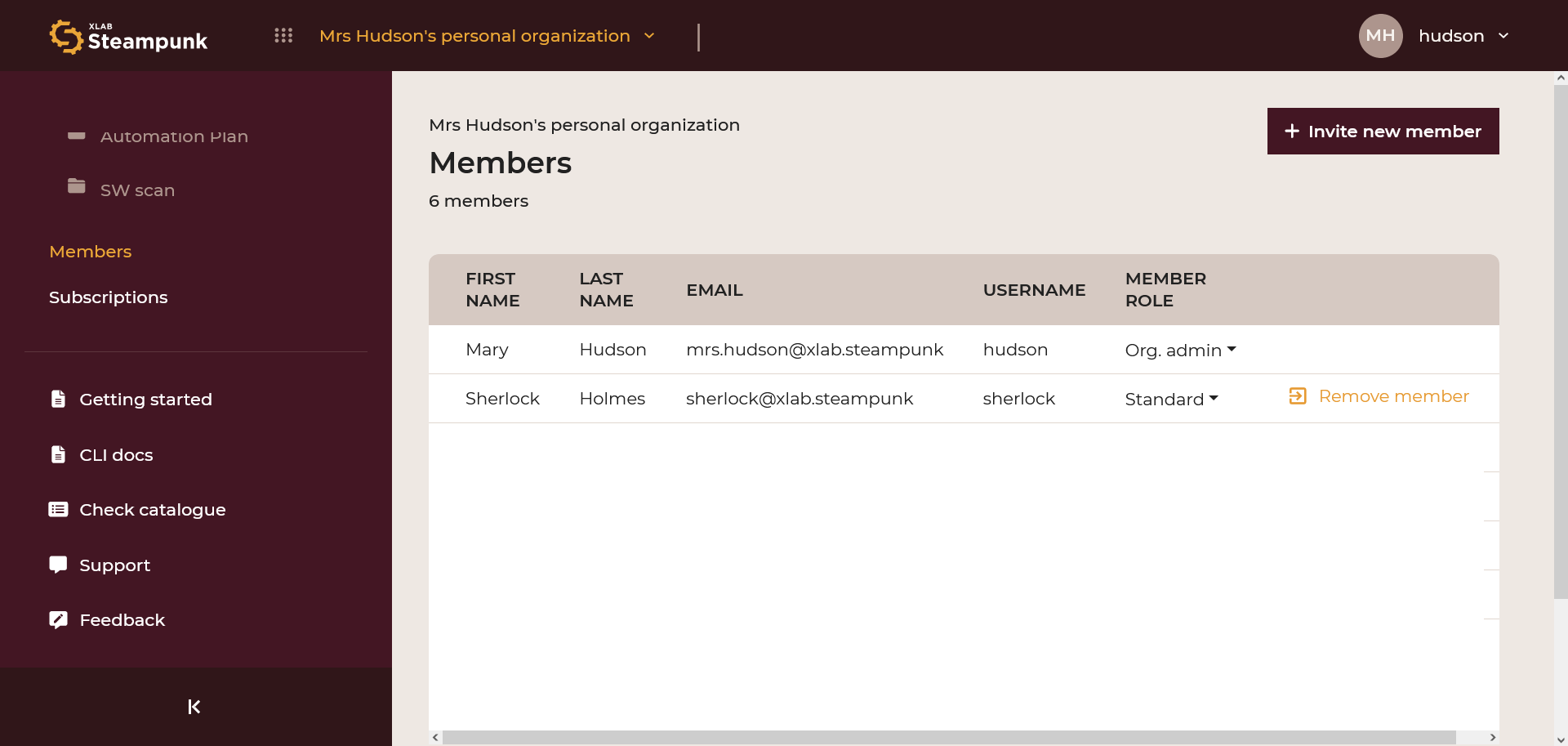
Add new members by clicking Invite new member:
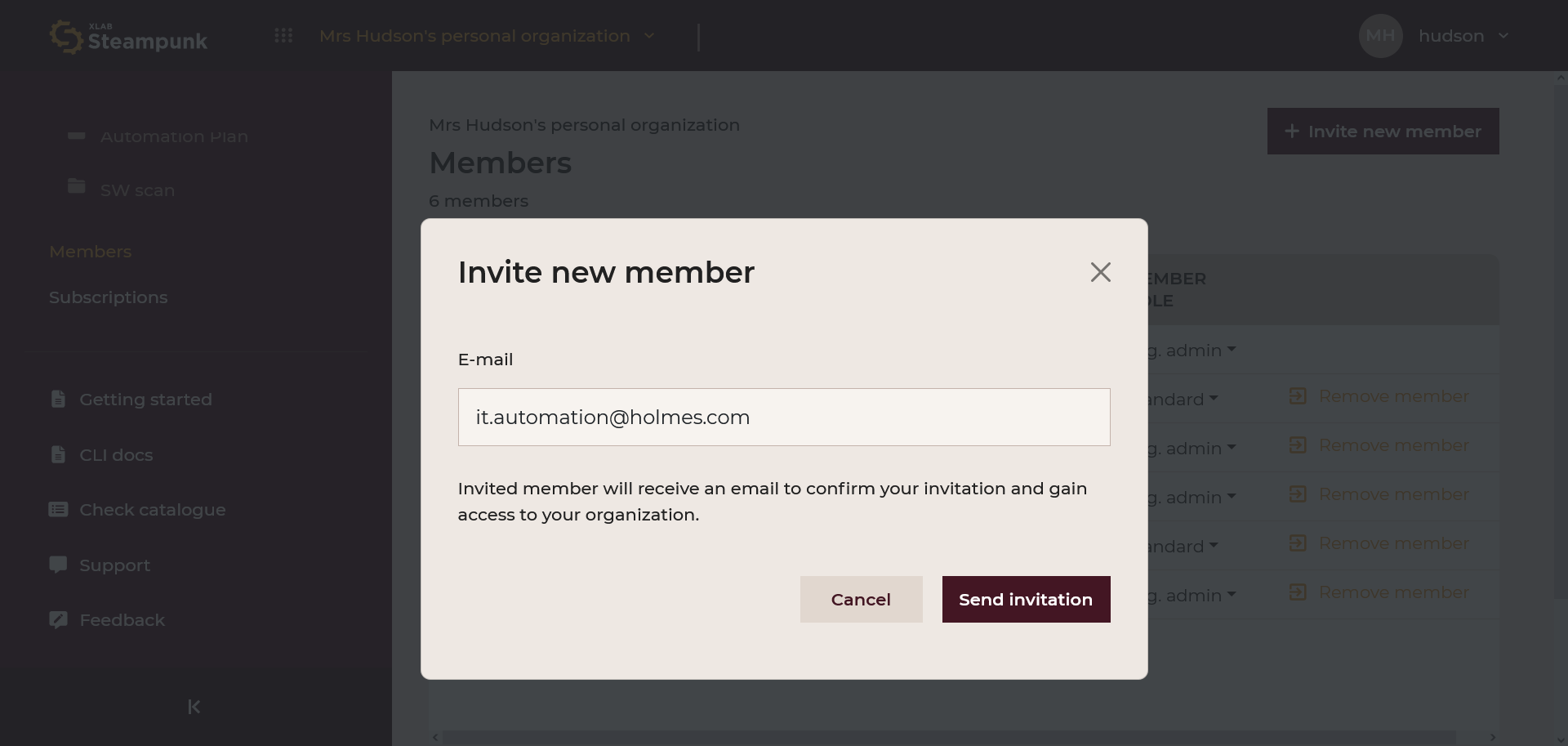
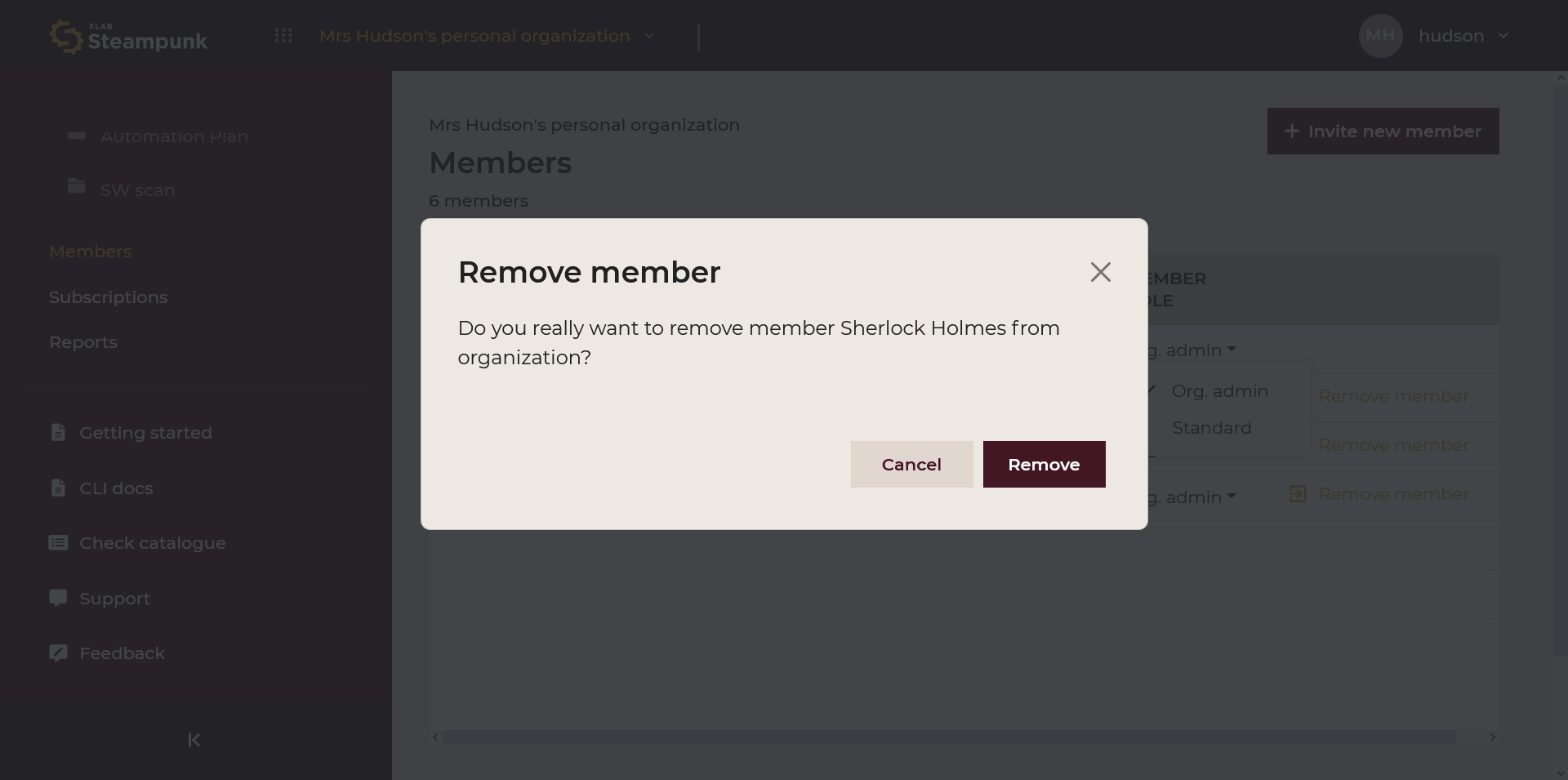
Remove members by clicking Remove member:
Reports
The Reports tab shows detailed analytics of users and their scan activity.
Note: Only organization admins can see Reports.
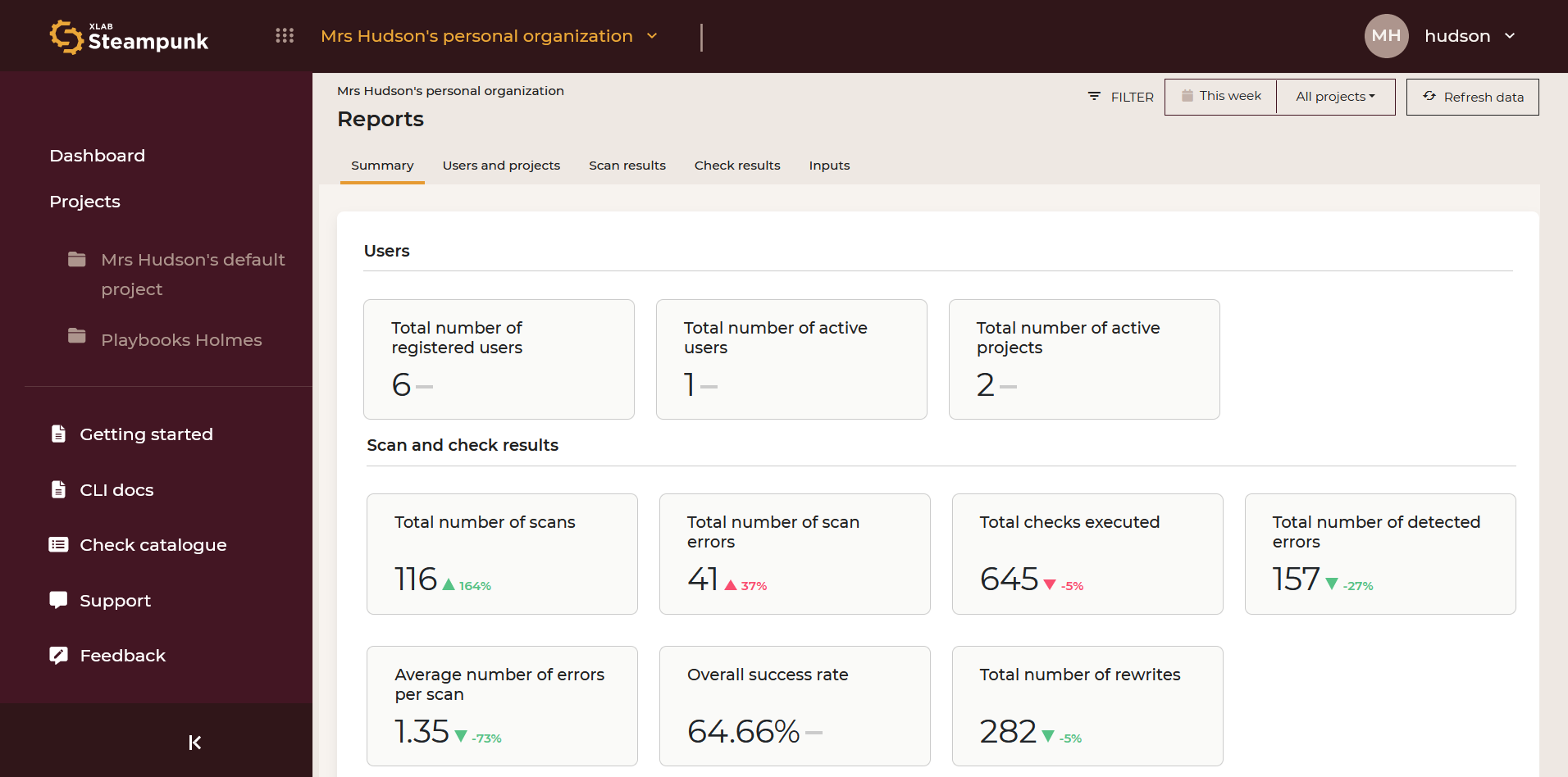
Summary
An overview of active users and projects, and scan and check results.
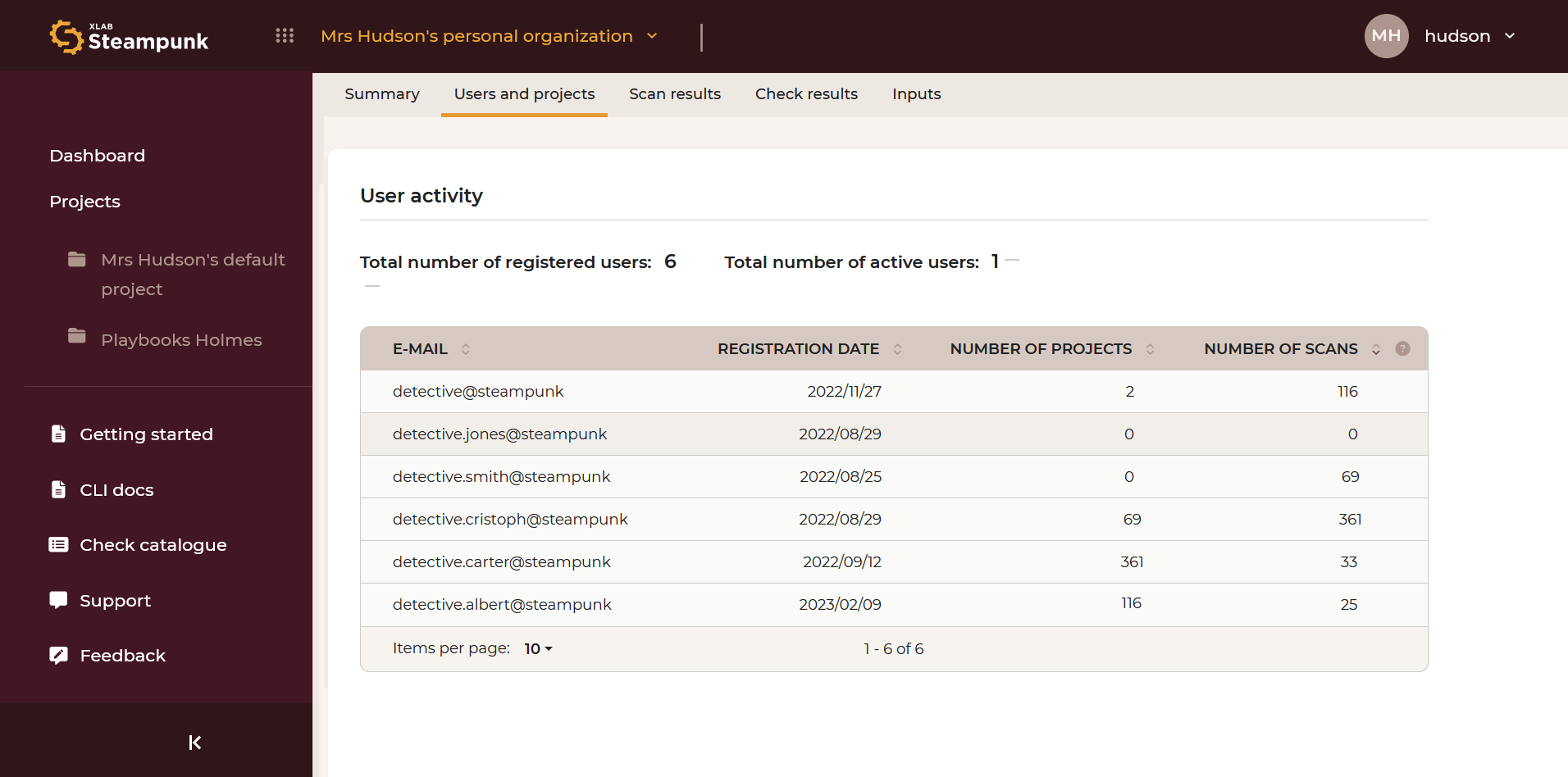
Users and Projects
A detailed view of users and projects.
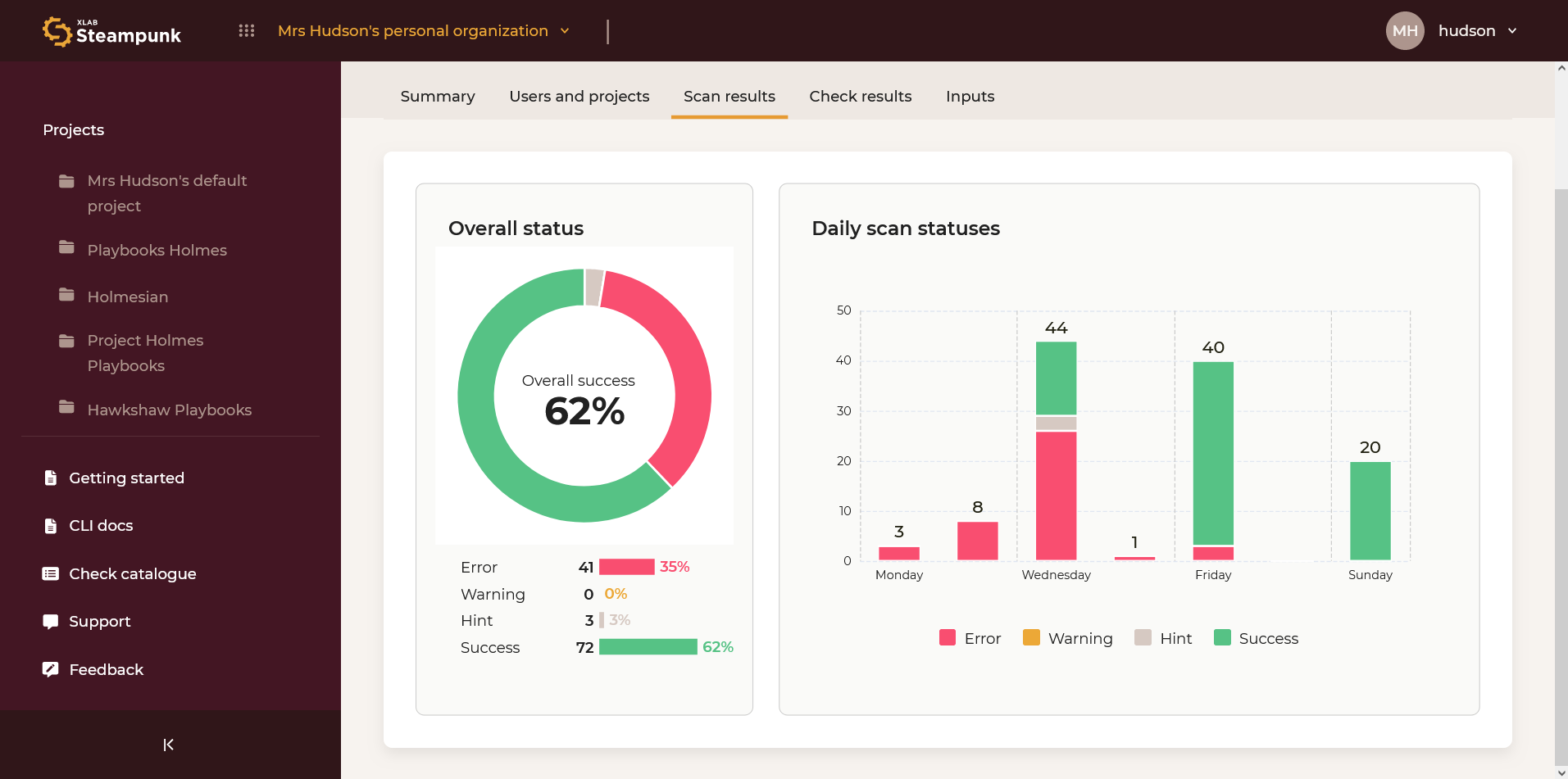
Scan results
A comprehensive overview of overall status and daily scan statuses.
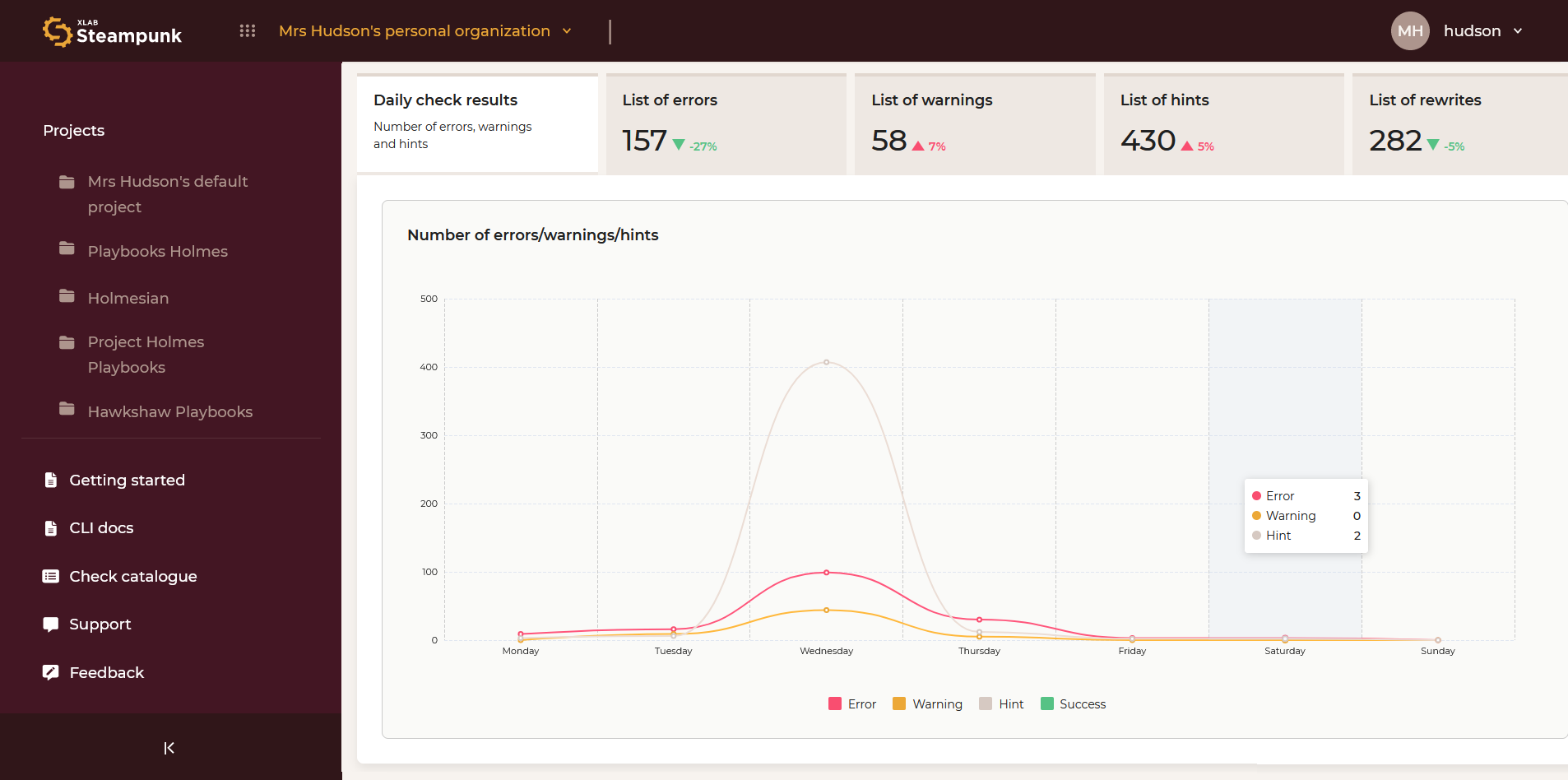
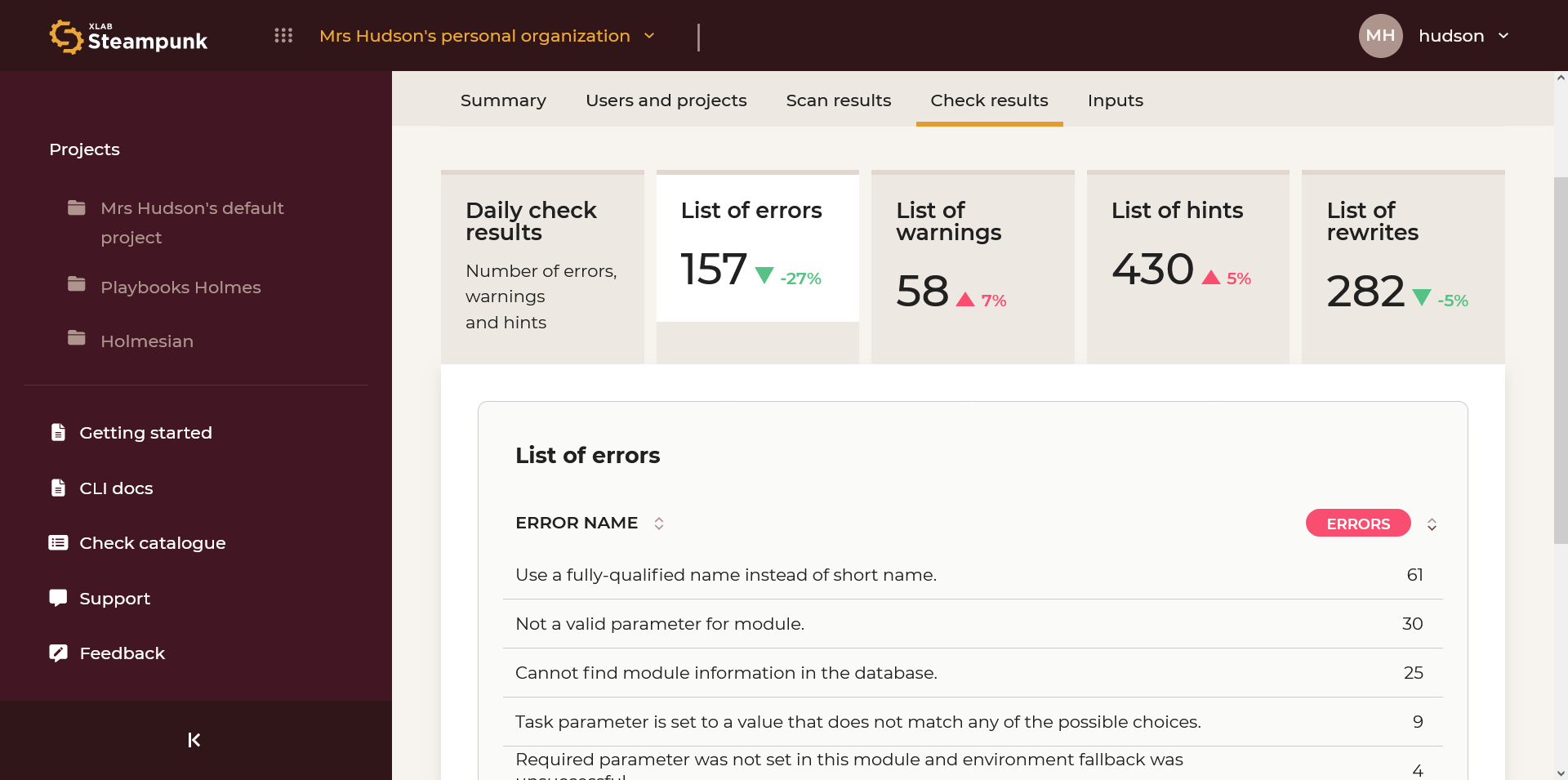
Check Results
An overview of all check results: daily check results and lists of errors, warnings, and hints.
Daily Check Results
Number of errors, warnings, and hints.
List of Errors
List of most common errors. By clicking the numeric code you can access the check in the Check catalogue.
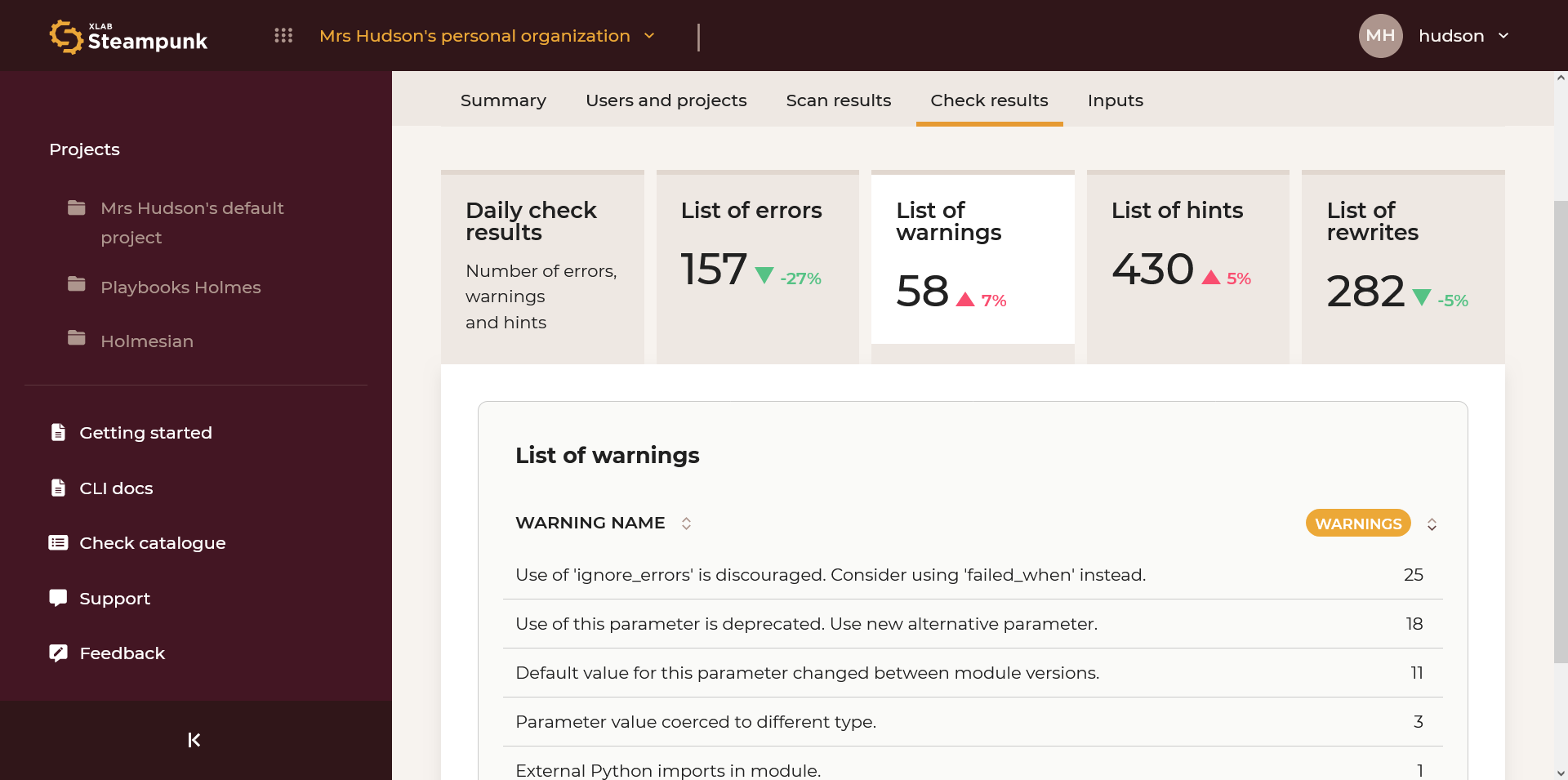
List of Warnings
List of most common warnings. By clicking the numeric code you can access the check in the Check catalogue.
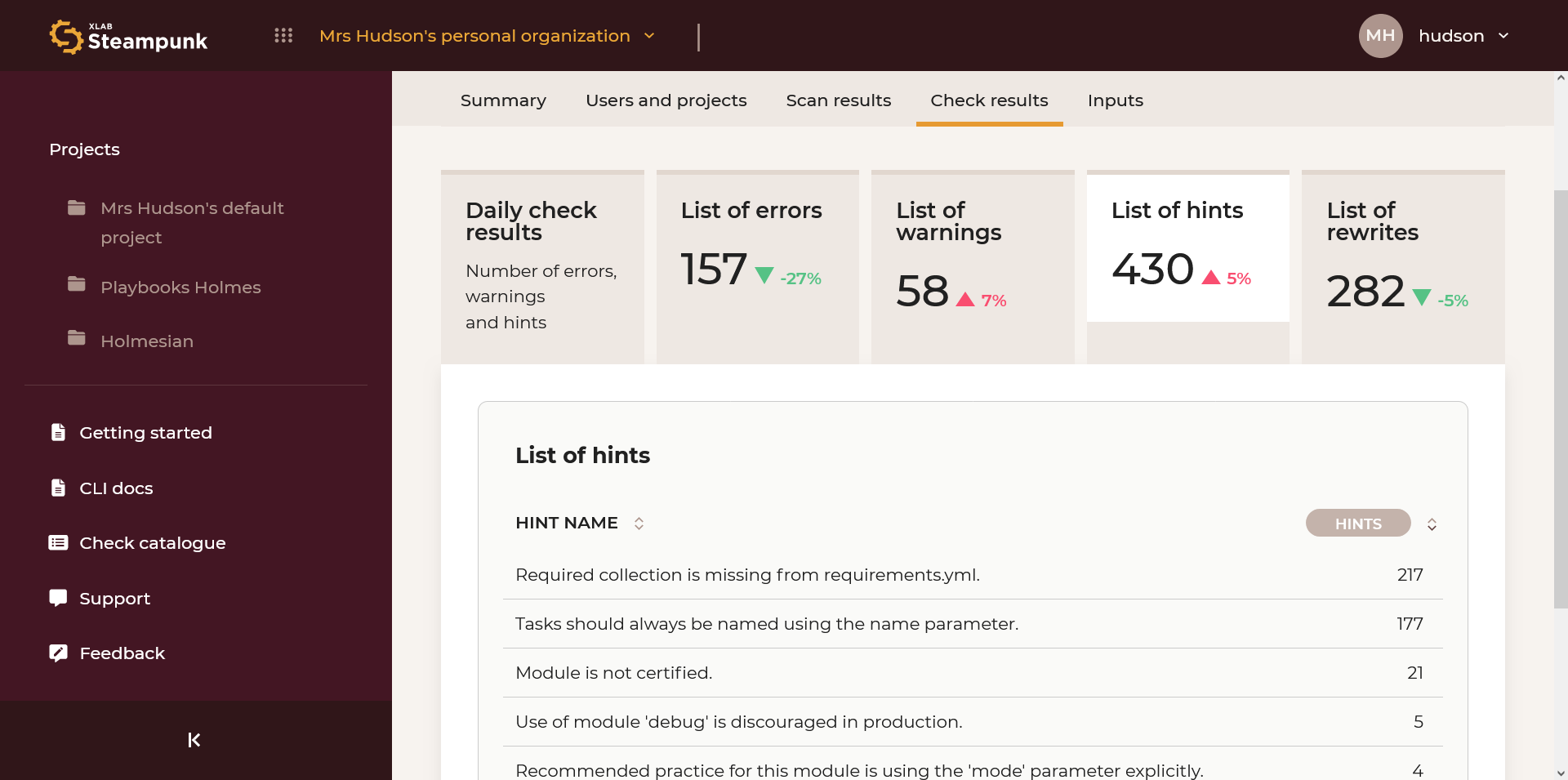
List of Hints
List of most common hints. By clicking the numeric code you can access the check in the Check catalogue.
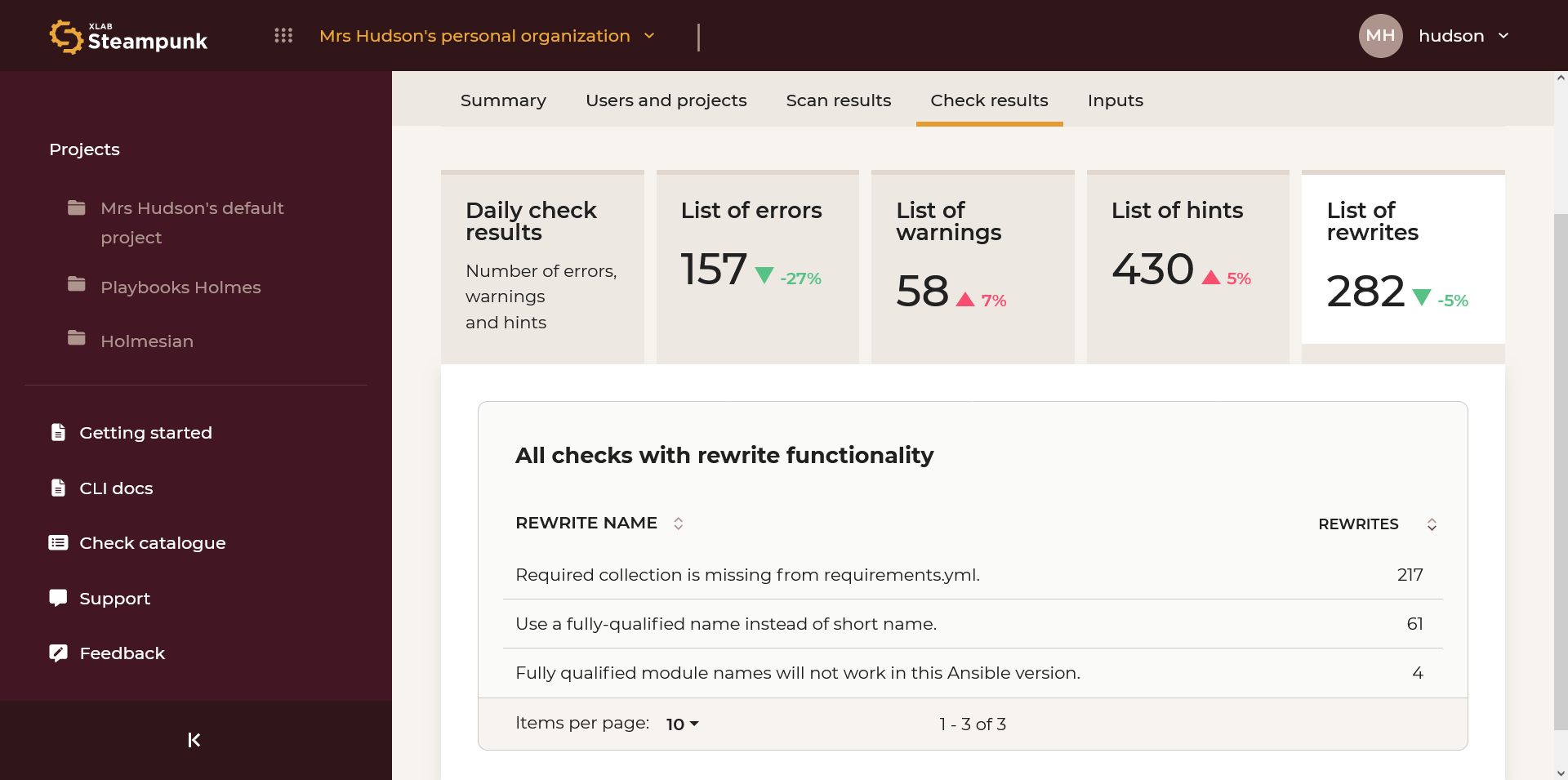
List of Rewrites
List of most common rewrites (automatically fixed errors). By clicking the numeric code you can access the check in the Check catalogue.
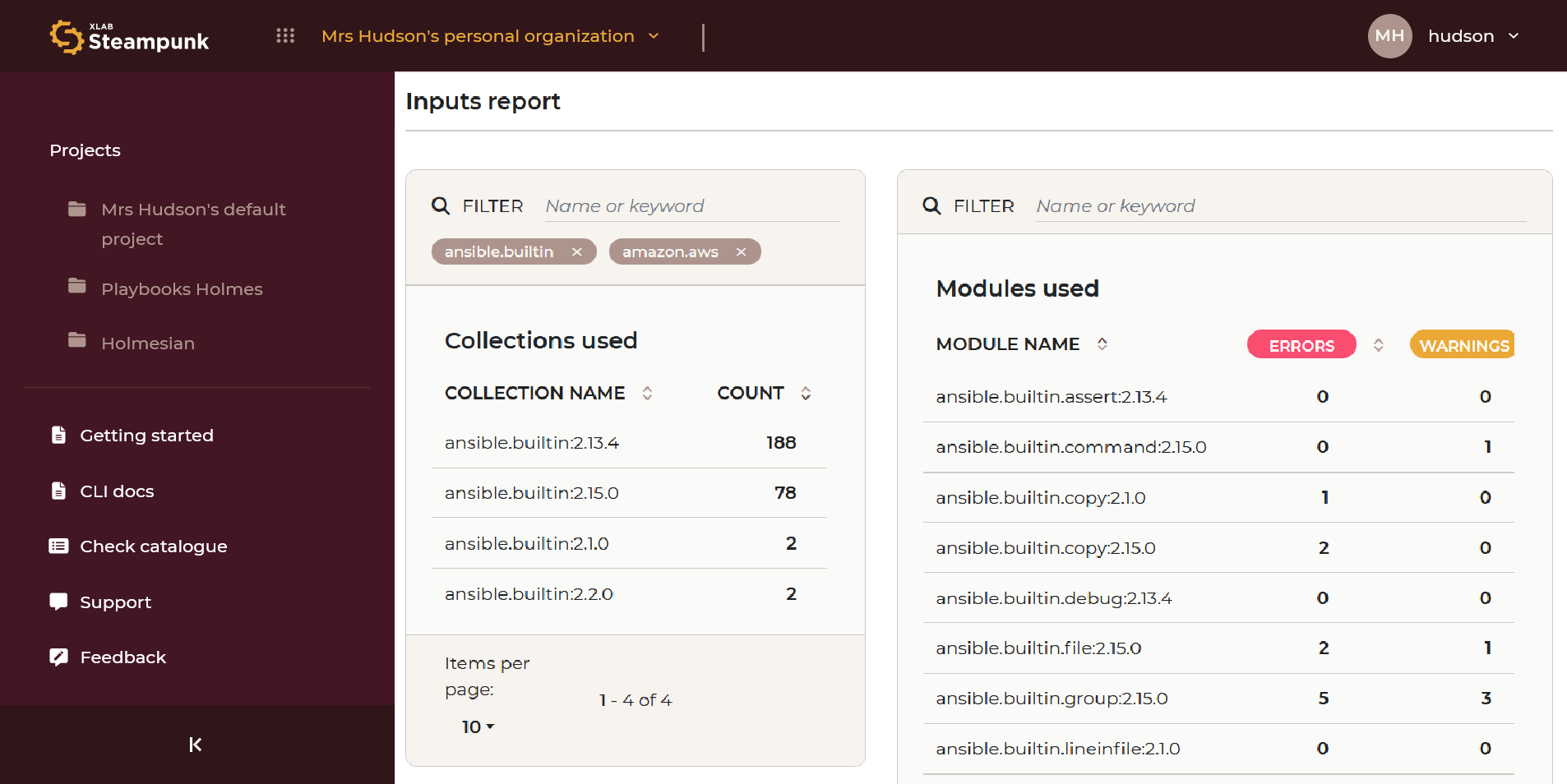
Inputs
The Inputs tab provides a way to manage and oversee the modules and collections with their corresponding version information. You can filter by name or keyword.
Custom Rules
Easily create and manage custom rules, written in Rego, a universal human-readable language to simplify policy management across your cloud-native stack; see how.
You can view and navigate applied custom policies on an organization or project level, accessible by clicking the drop-down menu. This enables you to review the logic and details of each custom policy directly in the app.
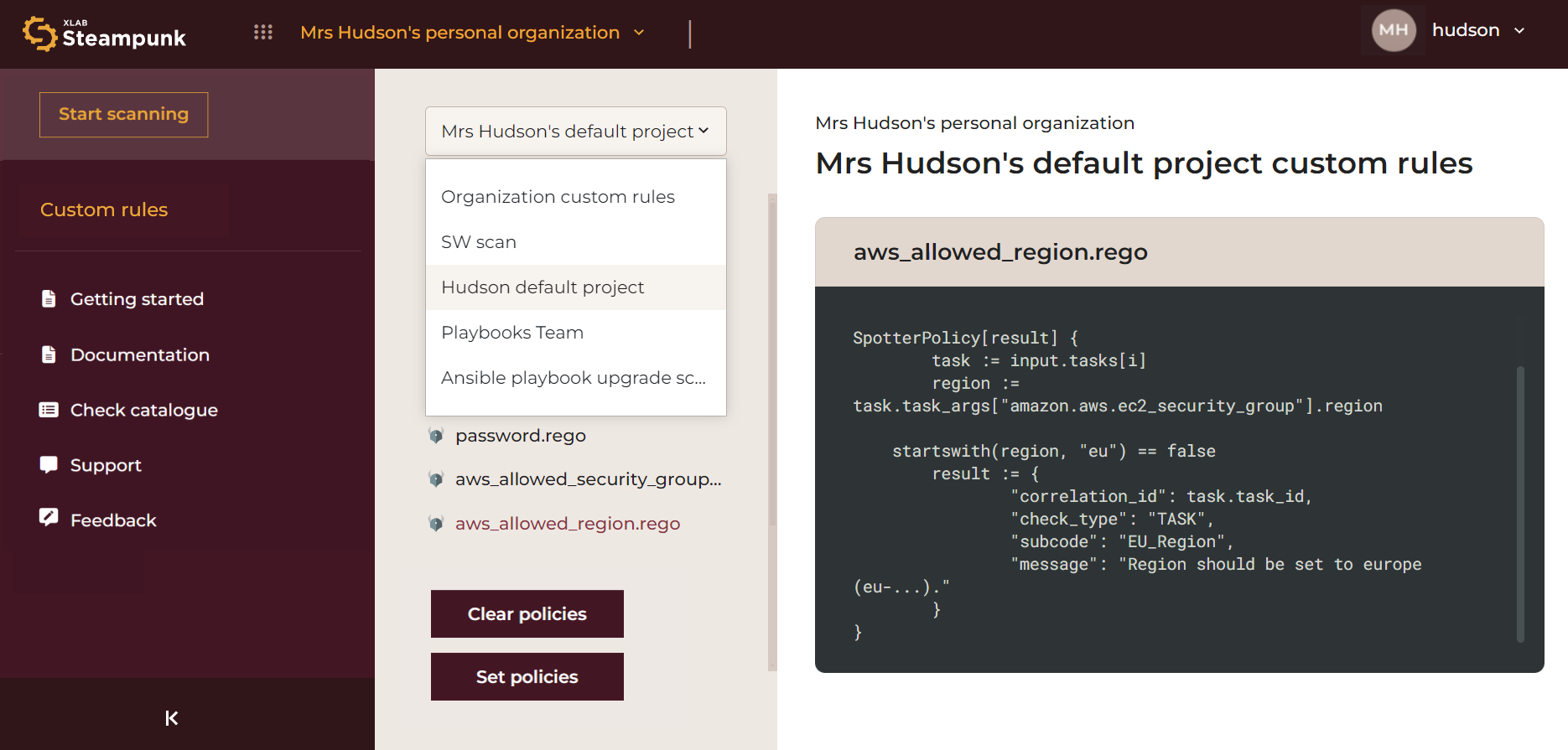
To upload a file or a folder containing policies, click the Set policies button. To remove all
existing policies, click the Clear policies button. Alternatively, policies can be managed via
the CLI by setting or clearing them as needed using the spotter policies set and
spotter policies clear commands.
Check Management
Achieve compliance and quality by centrally controlling which checks to skip and which to always enforce across all your automation workflows; see how
Integrations
Getting Started
The Getting Started guide showcases practical use cases and examples to help you start with Spotter.
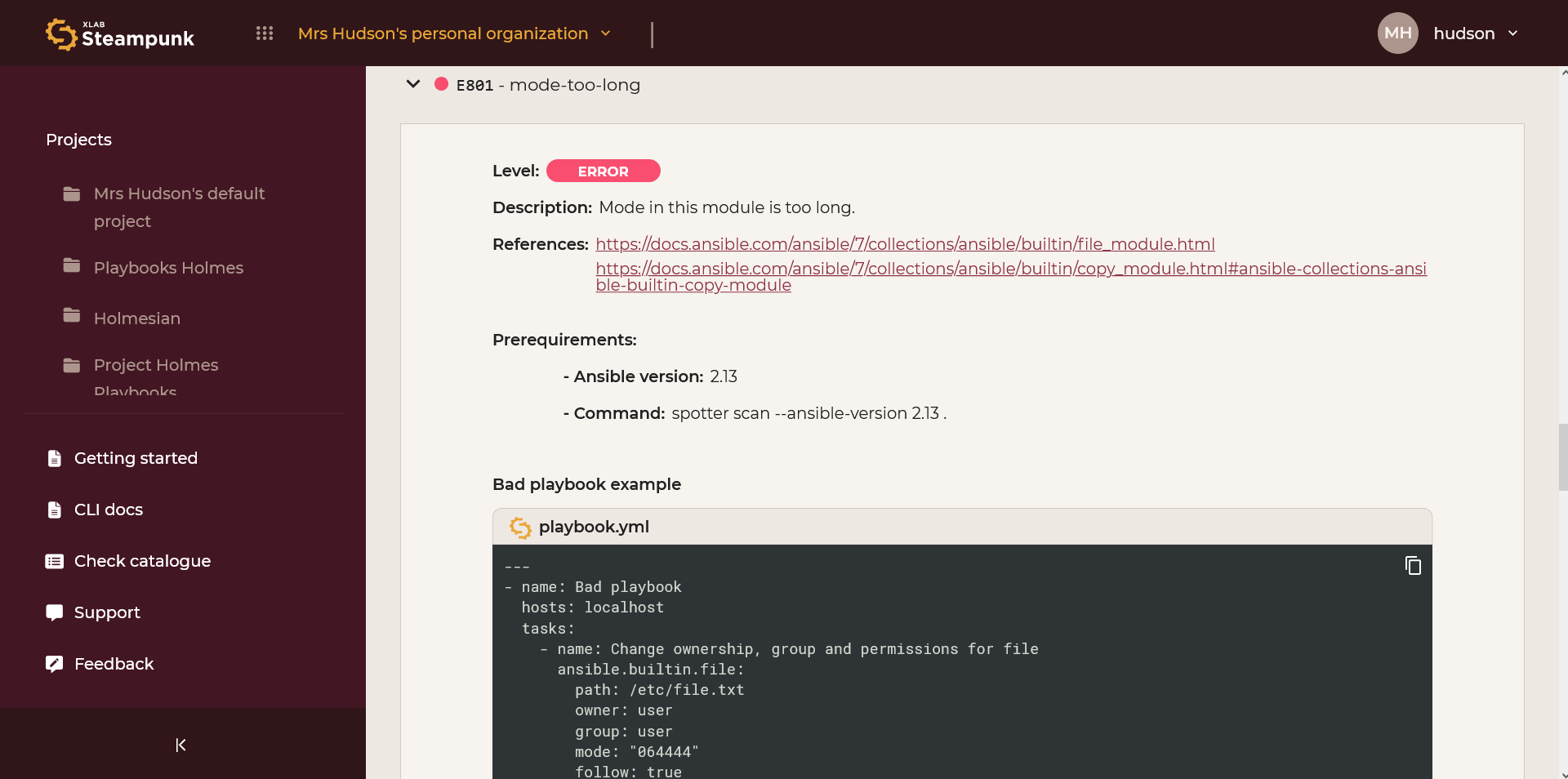
Check catalogue
Offers a comprehensive catalogue of all available checks in Spotter, including examples of "good and bad" Ansible Playbooks showcasing the check. You can filter by name, description, numeric code (e.g., W400), and level of the check.
Support
Contact us regarding any issues, questions, or business inquiries you might have.
Feedback
Share your feedback with us; we strive to improve Spotter. Your input is highly appreciated.